ZyXEL NWA50AX User Guide - Page 12
Introduction, 1.1 Overview, 1.2 Zyxel Device Roles
 |
View all ZyXEL NWA50AX manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 12 highlights
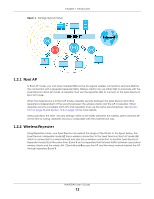
CHAPTER 1 Introduction 1.1 Overview The Zyxel Device can be managed in one of the following methods: remote management through Nebula Control Center (NCC) or local management in Standalone Mode. The Zyxel Device runs in standalone mode by default, but it is recommended to use NCC management if it is available for your device. For more information about Access Point (AP) management, see Section 2.1 on page 20. Use the Zyxel Device to set up a wireless network with other IEEE 802.11a/b/g/n/ac/ax compatible devices in either 2.4 GHz and 5 GHz networks or both at the same time. When two or more APs are interconnected, this network is called a Wireless Distribution System (WDS). See Section 1.2.2 on page 13 for more information on root and repeater APs and how to set them up. 1.2 Zyxel Device Roles This section describes some of the different roles that your Zyxel Device can take up within a network. Not all roles are supported by all models (see Section 1.4 on page 18). The Zyxel Device can serve as a: • Access Point (AP) - This is used to allow wireless clients to connect to the Internet. • Radio Frequency (RF) monitor - An RF monitor searches for rogue APs to help eliminate network threats if it supports monitor mode and rogue APs detection/containment. An RF monitor cannot simultaneously act as an AP. • Root AP - A root AP connects to the gateway or switch through a wired Ethernet connection and has wireless repeaters connected to it to extend its range. • Wireless repeater - A wireless repeater wirelessly connects to a root AP and extends the network's wireless range. The following figure shows a network setup that uses these different roles to create a secure Wireless Distribution System (WDS). The root AP (Y) is connected to a network with Internet access and has a wireless repeater (X) connected to it to expand the wireless network's range. Clients (A, B, and C) can access the wired network through the wireless repeater and/or root AP. If a client (D) tries to set up his own AP (R) with weak security settings, the network becomes exposed to threats. The RF monitor (M) scans the area to detect all APs, which can help the network administrator discover these rogue APs and remove them or use the NXC to quarantine them. NWA50AX User's Guide 12