McAfee M-1250 IPS Configuration Guide - Page 173
Managing DoS Learning Mode profiles, Group Name, Primary Interface, Delete, Save., DoS Profiles
 |
View all McAfee M-1250 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 173 highlights
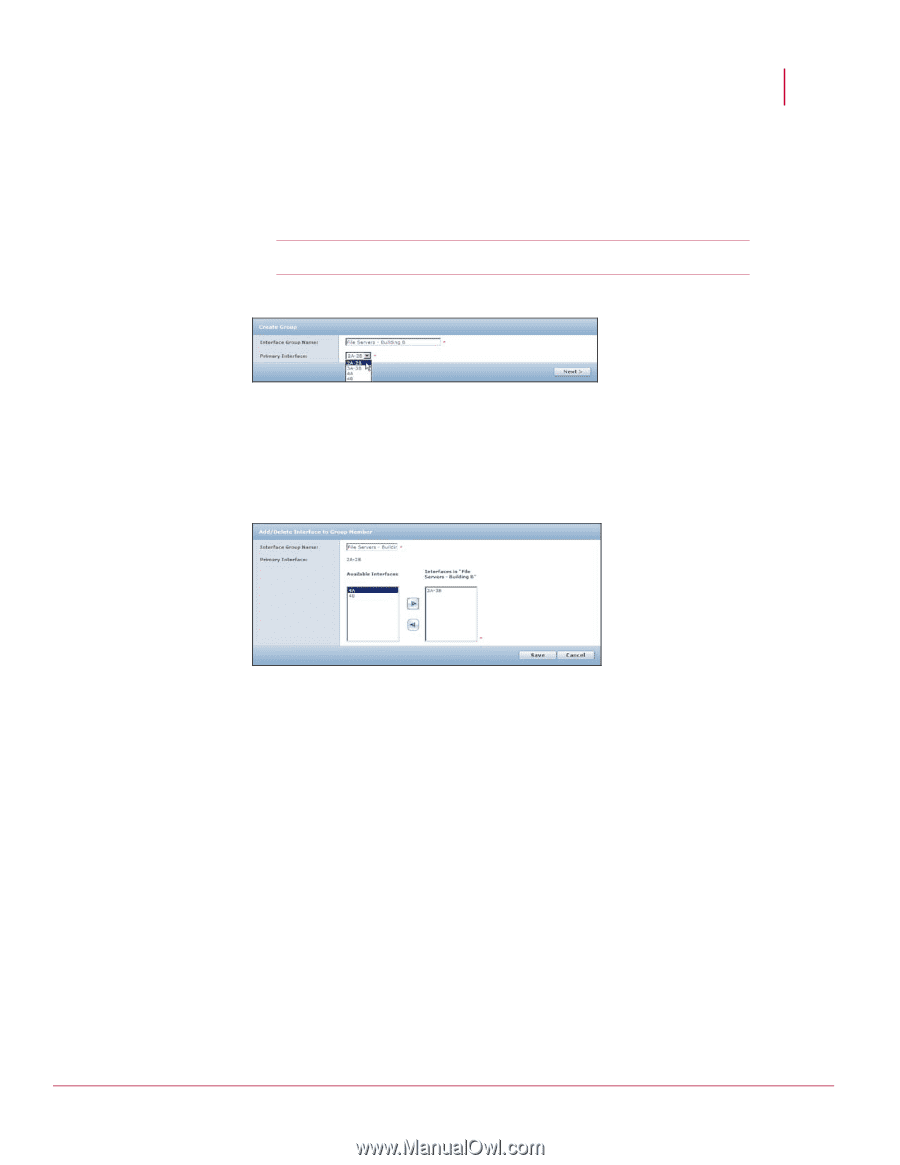
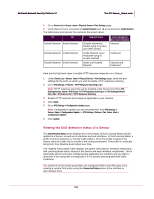
McAfee® Network Security Platform 5.1 The IPS Sensor_Name node 2 Click Add. 3 Type a Group Name. 4 Select a Primary Interface from the drop-down list. The primary interface may be a port pair (1A and 1B) or a single port (3B). The primary interface determines the policy that is enforced by the group. Note: An interface changed from Dedicated to VLAN or CIDR traffic types is not eligible for interface group combination until VLAN or CIDR IDs are added. 5 Click Next. Figure 176: Interface Group Creation 6 Select interfaces to add to the group. The primary is shown. 7 Click Add. Click Delete to remove any unwanted interfaces. 8 If interfaces are functioning as a port pair, they cannot be separated within an interface group. Figure 177: Add Interfaces To Interface Group 9 Click Save. 10 Download the changes to your Sensor by performing the steps in Updating the configuration of a Sensor. Managing DoS Learning Mode profiles The DoS Profiles action configures the DoS learning mode profile to restart or load from a previous profile. Denial of service (DoS) attacks interrupt network services by flooding a system or host with spurious traffic, which can overflow your system buffers and force you to take the system offline for repairs. Since a DoS profile can be configured for both learning and threshold modes, the Sensor keeps statistics for both modes. For Learning Mode, the Sensor monitors the network traffic and develops a "normal" baseline profile, called a long-term profile, by collecting statistics on a number of traffic measures over time. The initial learning time for the profile is typically two days. After that time, the system constantly updates this profile, which is kept on the internal Sensor flash, to keep an updated picture of the network. In real time, the Sensor develops a short-term profile, which is like an instant snapshot of the network 165