McAfee M-1250 IPS Configuration Guide - Page 250
Understanding attack descriptions, Policy, Threat Analyzer, Network Security Platform KnowledgeBase
 |
View all McAfee M-1250 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 250 highlights
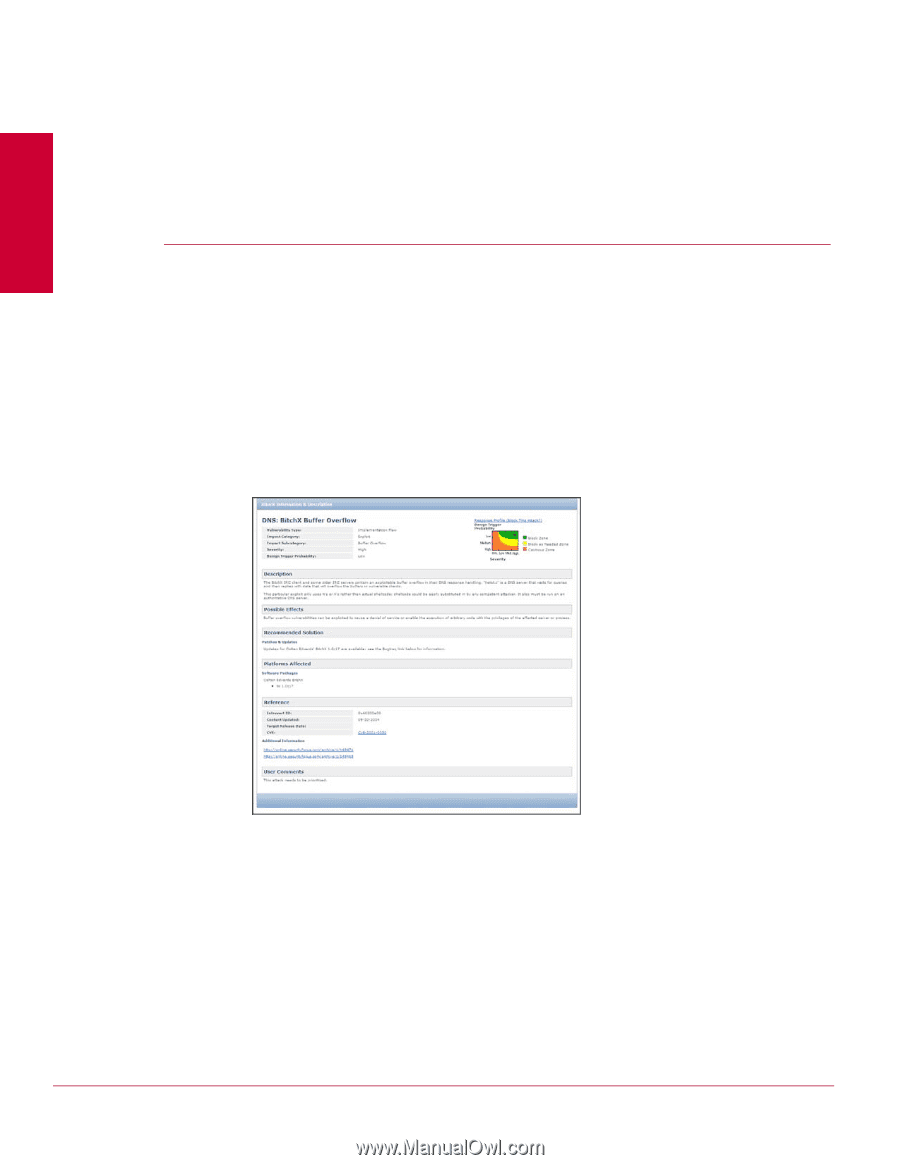
CHAPTER 4 Understanding attack descriptions Every attack detected by McAfee® Network Security Platform includes an attack description. The information in each attack description is designed to give reference to what the attack does and how to defend against the attack in the future. Attack descriptions can be accessed from a number of areas: • Policy: during policy viewing/creation. Includes all Exploit, DoS, and Reconnaissance attacks. • Threat Analyzer: within the details of a detected attack. • Network Security Platform KnowledgeBase: all entries within the Attack Encyclopedia. When you click an Attack Description button, a HTML file opens in an Internet Explorer browser window. Figure 234: Attack Description Example The Attack Information & Description fields are as follows: • Name: McAfee Network Security Platform-designated name for an attack. • Vulnerability Type: type of inherent system flaw that can be exploited by attackers. • Impact Category: type of impact that can be performed to a system. • Impact Subcategory: type of inherent system flaw that can be exploited by attackers. • Severity: malicious impact potential of the attack. High, Medium, Low. 242