McAfee M-1250 IPS Configuration Guide - Page 254
Remote Access, Read Exposure
 |
View all McAfee M-1250 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 254 highlights
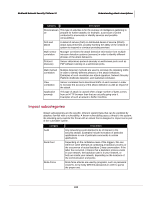
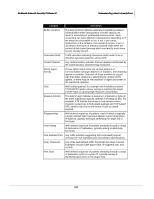
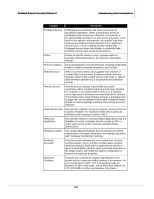
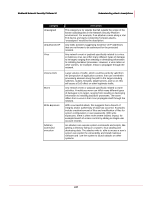
McAfee® Network Security Platform 5.1 Understanding attack descriptions Category Description Privileged Access Privileged access indicates the most serious type of successful exploitation, where unauthorized access to privileged accounts has been obtained. For example, a successful buffer overflow on a Unix server may open a root shell for the attacker. Alternatively, the attacker may have achieved successful privilege elevation from a legitimate user account, or from a remote access compromise. Privileged access allows the attacker to potentially take complete control of the compromised system. Probe Probes of specific service or host, typically based on specially constructed packets, for example unusual flag settings. Protocol Violation Unusual application protocol behaviors, including invalid field values or invalid command sequences, and so forth. Read Exposure With a successful attack, this suggests that a breach of confidentiality has occurred. Examples include directory traversal, dump of file content such as CGI script, or read of other sensitive data files such as password and database records. Remote Access Remote access indicates a potentially successful exploitation where unauthorized access has been obtained. For example, a successful buffer overflow on a Windows server may open a Windows command shell for the attacker. The remote access does not have to be for a privileged user to begin with, but an attacker may be able to perform further attacks to achieve privilege elevation once remote access is obtained. Restricted Access Any activities related to using any network resources that are explicitly forbidden. For example emails to/from particular addresses and browsing of specific URLs. Restricted Application Any activities related to running network applications that are forbidden by policy. Examples include running an IRC or music share server on the corporate network without authorization. Sensitive Content Any content keyword matches that are deemed to indicate transmission of sensitive information, for example document with "Company Confidential" marking. Shellcode Execution This kind of alert indicates the most severe form of buffer overflow attacks, that is, a buffer overflow attack carrying shellcode payload. Shellcode is a general term used for a piece of executable code that, upon successful execution on the target system, will modify the target's configuration or behavior for malicious purposes. Statistical Deviation Indicates that a significant change was detected in the packet rate for a particular traffic measure. For example, if in your normal flow of traffic, TCP SYN packets make up between 23-28% of the traffic, then a short-term measure of TCP SYN traffic at 40% may indicate a DoS attack. 246