McAfee M-1250 IPS Configuration Guide - Page 174
For more information, see Customizing Denial of Service DoS
 |
View all McAfee M-1250 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 174 highlights
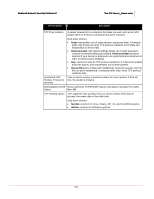
McAfee® Network Security Platform 5.1 The IPS Sensor_Name node traffic. The short-term profile is compared to the long-term profile and an alert is raised if the short-term statistics indicates a traffic surge that deviates too much from the long-term behavior. For Threshold Mode, the Sensor keeps track of the threshold limits you enabled for specific attacks. Together these two modes create one profile, which is saved to your Sensor's flash and can be uploaded to the Manager for future re-use. You can upload this saved profile later if you feel the baseline that had previously been created was more effective than a current profile. For more information, see Customizing Denial of Service (DoS) modes (on page 23). Note: DoS Copy feature is not supported on M-series and N-450 Sensors. To manage the DoS learning mode policies on a Sensor, do the following: 1 Click IPS Settings/Sensor_Name > Advanced Scanning > DoS Profiles (IPS Settings/Failover Pair Node/Sensor_Name > DoS Management > DoS Profiles in the case of a failover pair Sensor). The last DoS profile uploaded from the Sensor to Manager is listed under DoS Profiles Uploaded from Sensor to Manager. 2 Select one action from one of the following headings: Sensor DoS Profile Actions Re-learn Profile: restarts the learning process. The profile that has just been learned is erased, and a new profile is built. To start the re-learning process, select this option and click Update. Force Sensor into detection mode: activates Learning Mode detection for a Sensor without waiting the entire 48-hour learning time. Tip: McAfee recommends performing a "re-learn profile" when there is a network change (that is, moved Sensor from a lab environment to a production environment) or configuration change (changed the CIDR block of a subinterface) that causes a significant sudden traffic change to an interface/subinterface for which a profile has already been established (or in the process of initial learning). Without doing so, the Sensor may give false alarms or fail to detect attacks during a time period when it is adapting to the new network traffic conditions. 166