McAfee M-1250 IPS Configuration Guide - Page 256
into zombies or bots and transmits itself to other, infected computers
 |
View all McAfee M-1250 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 256 highlights
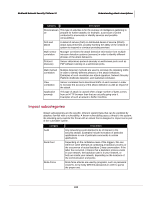
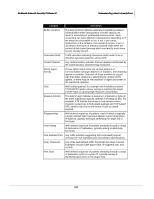
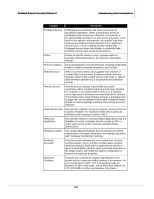
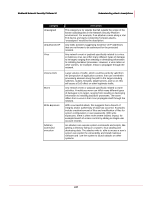
McAfee® Network Security Platform 5.1 Understanding attack descriptions Category Code execution Bot Service-sweep Description A vulnerability which can be exploited by malicious people to compromise a user's system. An attacker can execute malicious programs or code on a user's system. Successful exploitation allows execution of arbitrary code and possibly takes complete control of the affected system. Attacker can run code with elevated privileges. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. refers to a group of computers running or executing a program that allows an attacker to control the system remotely and make users execute commands like DOS. These commands are taken place in the IRC channel. A 'bot' is a type of malware which allows an attacker to gain complete control over the affected computer. Computers that are infected with a 'bot' are generally referred to as 'zombies'. Attackers are able to access lists of 'zombie' PC's and activate them to help execute DoS (denial-of-service) attacks against Web sites, host phishing attack Websites or send out thousands of spam email messages. A bot worm is a self-replicating malware program that resides in current memory (RAM), turns infected computers into zombies (or bots) and transmits itself to other computers. A bot worm may be created with the ultimate intention of creating a botnet that functions as a vehicle for the spread of viruses, Trojans and spam. An alert indicates that a client scans for services on your network or sub network thus leading to increased bandwidth corruption and increase in network traffic. It is usually generated by a P2P client. A Service Sweep is an attempt to determine if a service is running on a range of machines. The hacker will pick one port (usually 25-SMTP, 80-HTTP, or 139-NetBIOS SSN) and a range of IP addresses. A Ping Sweep is an attempt to see which machines in a network are on and responding. The easiest way to detect these in a trace is to look for ARP packets. So, create a filter looking for ARP requests. 248