McAfee Total Protection Service Product Guide
7
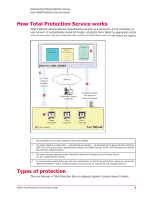
Enabling and disabling protection at the client computer
.........................................................................
109
Block and warn sites by safety ratings
...................................................................................................
109
Blocking or warning site access based on safety ratings
................................................................
111
Blocking or warning file downloads based on safety ratings
...........................................................
111
Blocking phishing pages
.............................................................................................................
112
Block and warn sites by content
............................................................................................................
112
Blocking or warning site access based on content
.........................................................................
113
Authorize and prohibit sites by URL or domain
.......................................................................................
113
How site patterns work
...............................................................................................................
114
Adding authorized and prohibited sites
........................................................................................
115
Customizing messages for users
............................................................................................................
115
Viewing browsing acitivity
.....................................................................................................................
116
Web Filtering report
.............................................................................................................................
117
Best practices (browser protection)
.......................................................................................................
117
Frequently asked questions
...................................................................................................................
118
Using the SaaS Vulnerability Scanning Service
...................................................
119
Vulnerability scanning features
..............................................................................................................
119
Certification programs
..........................................................................................................................
120
The SaaS vulnerability scanning widget and portal
..................................................................................
121
Accessing the SaaS vulnerability scanning portal
...........................................................................
122
Overview of scanning process
...............................................................................................................
122
Overview of the certification process
.....................................................................................................
123
Types of devices to scan
.......................................................................................................................
123
Types of scans
.....................................................................................................................................
124
Managing scan devices
.........................................................................................................................
125
Discovering IP addresses in a domain
..........................................................................................
126
Discovering IP addresses in a network
.........................................................................................
126
Adding devices to scan
...............................................................................................................
127
Configuring devices to accept scans
.............................................................................................
128
Creating device groups
...............................................................................................................
128
Changing device groups
..............................................................................................................
129
Deleting devices
........................................................................................................................
129
Performing scans
.................................................................................................................................
130
Starting a scan
...........................................................................................................................
130
Scheduling scans for devices
.......................................................................................................
131
How detections are reported
................................................................................................................
131
Viewing scan results
.............................................................................................................................
132
Viewing results for audit scans
....................................................................................................
132
Viewing results for DNS discovery on domains
..............................................................................
133
Viewing results for network discovery scans
.................................................................................
133