Ricoh Aficio SP C820DN Design Guide - Page 75
Data Flow
 |
View all Ricoh Aficio SP C820DN manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 75 highlights
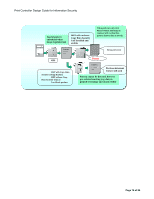
Print Controller Design Guide for Information Security visible when a copy of the document is made. This optional text field can be set to a number of different character strings to suit the operator's needs, such as "Copying of this document is prohibited", the date on which the document was created, or the name of the user who created the document. By making this information visible, it is possible to further deter the unauthorized copying of documents. Note: - The exact appearance of the optional text string (size, image density, etc.) will depend on the type and condition of the machine duplicating the image. - Even while the optional Copy Data Security Unit is still installed, the Machine Administrator can disable the detection/graying function using the machine settings (there is no need to remove the unit to do so). 3-2-2 Data Flow Marking: The data flow for when the Copy Data Security feature is selected at the time a print job is performed is virtually the same as that of regular print jobs (see 2.2 Printer). The printer language-encoded data sent from the host computer is interpreted by the language processing subsystem, after which it is converted into image data. It is then combined with the background pattern selected by the user and stored temporarily in the Page Memory in binary bitmap format. Detection, replacing image with vertical line pattern: The optional Copy Data Security Unit functions as an image processing component during the scanning of the image. As the scanning engine scans the image, the Copy Data Security Unit examines the data for the presence of an embedded pattern. If the unit detects the presence of the pattern, which in effect alerts the MFP that this is a confidential document, the buzzer is sounded and the image is replaced with the vertical line pattern. Following this, an entry for the event itself is stored in the access log, along with the username. Page 75 of 86