Lexmark MS517 Embedded Web Server--Security: Administrator s Guide - Page 5
Managing authentication and authorization methods, Understanding the basics
 |
View all Lexmark MS517 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 5 highlights
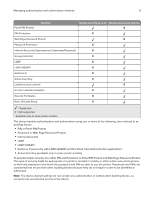
Managing authentication and authorization methods 5 Managing authentication and authorization methods Understanding the basics Secure a printer through the Embedded Web Server by defining the users who can use the printer and the functions that they can access. This process involves the components called Authentication, Authorization, and Groups. Create a plan that identifies who the users are and what they need to do before configuring printer security. Items to consider might include the following: • The location of the printer and whether authorized persons have access to that area • Sensitive documents that are sent to or stored on the printer • Information security policies of your organization Authentication and authorization Authentication is the method by which a system securely identifies a user. Authorization specifies which functions are available to a user who has been authenticated by the system. This set of authorized functions is also referred to as "permissions." There are two levels of security that are supported based on the product definition. Simple security only supports internal device authentication and authorization methods. More advanced security permits internal and external authentication and authorization as well as additional restriction capability for management, function, and solution access. Advanced security is supported for those devices that permit the installation of additional solutions to the device. Simple security uses Panel PIN Protect to restrict user access to the printer control panel and Web Page Password Protect to restrict administrator access to the device. For more information, see "Creating a PIN and applying access control restrictions" on page 9 and "Creating a Web page password and applying access control restrictions" on page 8. Advanced‑security devices support the following: • PIN and password restrictions in addition to the other authentication and authorization specified • Multiple local authentication functions that support PIN, password, and user name-password combinations • Standard network authentication through LDAP, LDAP+GSSAPI, Kerberos, and Active Directory® Authorization can be specified individually or by groups (either local or network). Devices that support advanced-level security are capable of running installed solutions, which permit usage of card readers to provide advanced two-factor authentication.