Netgear WGPS606 WGPS606 User Manual - Page 51
WPA Authentication: Enterprise-level User Authentication via 802.1x/EAP and RADIUS - login
 |
UPC - 606449039542
View all Netgear WGPS606 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 51 highlights
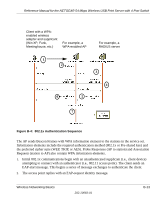
Reference Manual for the NETGEAR 54 Mbps Wireless USB Print Server with 4-Port Switch The supplicant in the station uses the authentication and cipher suite information contained in the information elements to decide which authentication method and cipher suite to use. For example, if the access point is using the Pre-shared key method then the supplicant need not authenticate using full-blown 802.1X. Rather, the supplicant must simply prove to the access point that it is in possession of the pre-shared key. If the supplicant detects that the service set does not contain a WPA information element then it knows it must use pre-WPA 802.1X authentication and key management in order to access the network. • Key management. WPA features a robust key generation/management system that integrates the authentication and data privacy functions. Keys are generated after successful authentication and through a subsequent 4-way handshake between the station and Access Point (AP). • Data Privacy (Encryption). Temporal Key Integrity Protocol (TKIP) is used to wrap WEP in sophisticated cryptographic and security techniques to overcome most of its weaknesses. • Data integrity. TKIP includes a message integrity code (MIC) at the end of each plaintext message to ensure messages are not being spoofed. WPA Authentication: Enterprise-level User Authentication via 802.1x/EAP and RADIUS Wireless LAN WPA enabled wireless client with "supplicant" WPA enabled Access Point using pre-shared key or 802.1x Figure B-3: WPA Overview Wired Network with Optional 802.1x Port Based Network Access Control TCP/IP Ports Closed Until TCP/IP Ports Opened After Authenticated RADIUS Server Login Authentication Optional Certificate Authority (eg Win Server, VeriSign, etc) Wireless Networking Basics 202-10083-01 B-11