TP-Link T1700G-28TQ T1700G-28TQ V1 User Guide - Page 225
Port Config
 |
View all TP-Link T1700G-28TQ manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 225 highlights
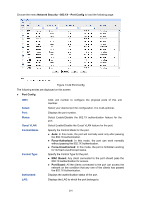
The following entries are displayed on this screen: Global Config 802.1X: Auth Method: Handshake: Enable/Disable the 802.1X function. Select the Authentication Method from the pull-down list. EAP: IEEE 802.1X authentication system uses extensible authentication protocol (EAP) to exchange information between the switch and the client. The EAP protocol packets with authentication data can be encapsulated in the advanced protocol (such as RADIUS) packets to be transmitted to the authentication server. PAP: IEEE 802.1X authentication system uses extensible authentication protocol (EAP) to exchange information between the switch and the client. The transmission of EAP packets is terminated at the switch and the EAP packets are converted to the other protocol (such as RADIUS) packets for transmission. Enable/Disable the Handshake feature. The Handshake feature is used to detect the connection status of the TP-LINK 802.1X Client with the switch. Please disable Handshake feature if you are using other client software instead of TP-LINK 802.1X Client. Guest VLAN: Guest VLAN ID: Enable/Disable the Guest VLAN feature. Enter your desired VLAN ID to enable the Guest VLAN feature. The supplicants in the Guest VLAN can access the specified network source. Authentication Config Quiet: Quiet Period: Retry Times: Supplicant Timeout: Server Timeout: Enable/Disable the Quiet timer. Specify a value for Quiet Period. Once the supplicant failed to the 802.1X Authentication, then the switch will not respond to the authentication request from the same supplicant during the Quiet Period. Specify the maximum transfer times of the repeated authentication request. Specify the maximum time for the switch to wait for the response from supplicant before resending a request to the supplicant. Specify the maximum time for the switch to wait for the response from authentication server before resending a request to the authentication server. 13.5.2 Port Config On this page, you can configure the 802.1X features for the ports basing on the actual network. 215