TP-Link TL-SG3210 TL-SG3210 V1 User Guide - Page 162
Network Security, DoS Defend, Con Defend Table
 |
View all TP-Link TL-SG3210 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 162 highlights
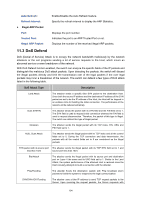
SYN-ACK packets. Since the IP address is fake, no response will be returned. The Server will keep on sending SYN-ACK packets. If the attacker sends overflowing fake request packets, the network resource will be occupied maliciously and the requests of the legal clients will be denied. Table 11-1 Defendable DoS Attack Types On this page, you can enable the DoS Defend type appropriate to your need. Choose the menu Network Security→DoS Defend→DoS Defend to load the following page. Figure 11-16 DoS Defend The following entries are displayed on this screen: ¾ Configure DoS Defend: Enable/Disable DoS Defend function. ¾ Defend Table Select: Select the entry to enable the corresponding Defend Type. Defend Type: Displays the Defend Type name. Tips: You are suggested to take the following further steps to ensure the network security. 1. It's recommended to inspect and repair the system vulnerability regularly. It is also necessary to install the system bulletins and backup the important information in time. 2. The network administrator is suggested to inspect the physic environment of the network and block the unnecessary network services. 3. Enhance the network security via the protection devices, such as the hardware firewall. 155