ZyAIR G-160 User’s Guide
List of Figures
xi
List of Figures
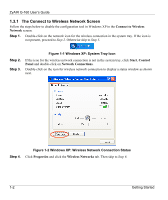
Figure 1-1 Windows XP: System Tray Icon
.................................................................................................
1-2
Figure 1-2 Windows XP: Wireless Network Connection Status
..................................................................
1-2
Figure 1-3 Windows XP: Connect to Wireless Network
..............................................................................
1-3
Figure 1-4 Windows XP: Wireless Network Connection Properties
............................................................
1-4
Figure 1-5 ZyAIR Utility: System Tray Icon
...............................................................................................
1-4
Figure 2-1 Ad-hoc Network Example
..........................................................................................................
2-2
Figure 2-2 BSS Example
..............................................................................................................................
2-2
Figure 2-3 Infrastructure Network Example
................................................................................................
2-3
Figure 2-4 Roaming Example
......................................................................................................................
2-4
Figure 2-5 RTS Threshold
............................................................................................................................
2-5
Figure 2-6 Wireless LAN Security Levels
...................................................................................................
2-6
Figure 2-7
WPA - PSK Authentication
.........................................................................................................
2-9
Figure 2-8 WPA with RADIUS Application Example
...............................................................................
2-10
Figure 2-9 Main
.........................................................................................................................................
2-11
Figure 2-10 Main: New Connection
...........................................................................................................
2-13
Figure 2-11 Main: Advanced
......................................................................................................................
2-16
Figure 2-12 Advanced
................................................................................................................................
2-17
Figure 2-13 Privacy
....................................................................................................................................
2-19
Figure 2-14 WEP Configuration
................................................................................................................
2-21
Figure 2-15 802.1X Configuration
.............................................................................................................
2-23
Figure 2-16 PSK Configuration
.................................................................................................................
2-25
Figure 2-17 Statistics
.................................................................................................................................
2-26
Figure 2-18 About
......................................................................................................................................
2-28
Figure 3-1 Confirm Uninstallation
...............................................................................................................
3-1