ZyXEL G-162 User Guide - Page 88
WPA or WPA2 applies IEEE 802.1x and Extensible Authentication Protocol EAP to authenticate
 |
View all ZyXEL G-162 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 88 highlights
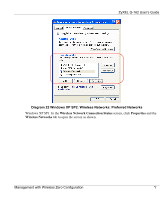
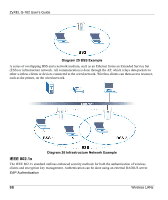
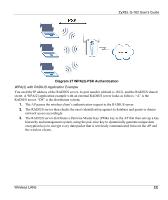
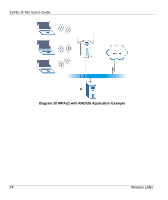
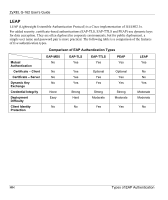
ZyXEL G-162 User's Guide The encryption mechanisms used for WPA and WPA-PSK are the same. The only difference between the two is that WPA-PSK uses a simple common password, instead of user-specific credentials. The commonpassword approach makes WPA-PSK susceptible to brute-force password-guessing attacks but it's still an improvement over WEP as it employs an easier-to-use, consistent, single, alphanumeric password. User Authentication WPA or WPA2 applies IEEE 802.1x and Extensible Authentication Protocol (EAP) to authenticate wireless clients using an external RADIUS database. If both an AP and the wireless clients support WPA2 and you have an external RADIUS server, use WPA2 for stronger data encryption. If you don't have an external RADIUS server, you should use WPA2 -PSK (WPA2 -Pre-Shared Key) that only requires a single (identical) password entered into each access point, wireless gateway and wireless client. As long as the passwords match, a wireless client will be granted access to a WLAN. If the AP or the wireless clients do not support WPA2, just use WPA or WPA-PSK depending on whether you have an external RADIUS server or not. Select WEP only when the AP and/or wireless clients do not support WPA or WPA2. WEP is less secure than WPA or WPA2. WPA(2)-PSK Application Example A WPA(2)-PSK application looks as follows. 1. First enter identical passwords into the AP and all wireless clients. The Pre-Shared Key (PSK) must consist of between 8 and 63 ASCII characters (including spaces and symbols). 2. The AP checks each wireless client's password and (only) allows it to join the network if the password matches. 3. The AP derives and distributes keys to the wireless clients. 4. The AP and wireless clients use the TKIP or AES encryption process to encrypt data exchanged between them. DD Wireless LANs