Lexmark X925 Common Criteria Installation Supplement and Administrator Guide - Page 49
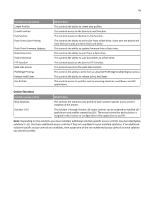
specific access controls are available, then assign one of the ten numbered access controls to each
 |
View all Lexmark X925 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 49 highlights
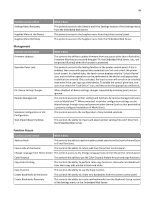
49 Function access control Create Profiles E‑mail Function Fax Function Flash Drive Color Printing Flash Drive Firmware Updates Flash Drive Print Flash Drive Scan FTP Function Held Jobs Access PictBridge Printing Release Held Faxes Use Profiles What it does This controls the ability to create new profiles. This controls access to the Scan to E‑mail function. This controls access to the Scan to Fax function. This controls the ability to print color from a flash drive. Users who are denied will have their print jobs printed in black and white. This controls the ability to update firmware from a flash drive. This controls the ability to print from a flash drive. This controls the ability to scan documents to a flash drive. This controls access to the Scan to FTP function. This protects access to the Held Jobs function. This controls the ability to print from an attached PictBridge‑enabled digital camera. This controls the ability to release (print) held faxes. This controls access to profiles, such as scanning shortcuts, workflows, and eSF applications. Device Solutions Function access control New Solutions Solution 1-10 What it does This controls the initial security profile of each solution‑specific access control installed on the printer. The Solution 1 through Solution 10 access controls can be assigned to installed eSF applications and profiles created by LDSS. The access control for each solution is assigned in the creation or configuration of the application or profile. Note: Depending on the solutions you have installed, additional solution‑specific access controls may be listed below solutions 1-10. Use these additional access controls if they are available for your installed solutions. If no additional solution‑specific access controls are available, then assign one of the ten numbered access controls to each solution you want to protect.