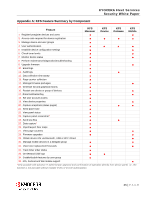
Kyocera ECOSYS P2235dn Kyocera Fleet Services KFS Security White Paper - Page 25
Microsoft, Azure, Security
 |
View all Kyocera ECOSYS P2235dn manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 25 highlights
KYOCERA Fleet Services Security White Paper contained in print jobs. However, users must determine if special precautions should be implemented to comply with private, personal or confidential information regulations. Microsoft® Azure® Security KFS relies on the Microsoft Azure platform for the protection, at the infrastructure level, of its cloud services and virtual machines (VM) against malicious attempts, such as distributed denial-of-service (DDoS) and DNS attacks. Azure's defense against DDoS is part of its continuous monitoring process and is continually improved through penetration-testing. It is designed to not only withstand attacks from the outside, but also from other Azure tenants. Furthermore, Microsoft's Azure datacenter operations implement comprehensive information security policies and processes using standardized industry control frameworks, such as ISO 27001, SOC 1, and SOC 2. Third-party auditors regularly certify Microsoft's adherence to these standards for both the physical and virtual aspects of Azure infrastructure. Thus, KFS is continually diagnosed for the detection of such typical vulnerabilities of a web application as privilege escalation, directory traversal, code injection, crosssite scripting, etc. Note: • For general information and links about Azure, please visit http://azure.microsoft.com. 24 | P A G E