TRENDnet TEW-601PC User Guide - Page 15
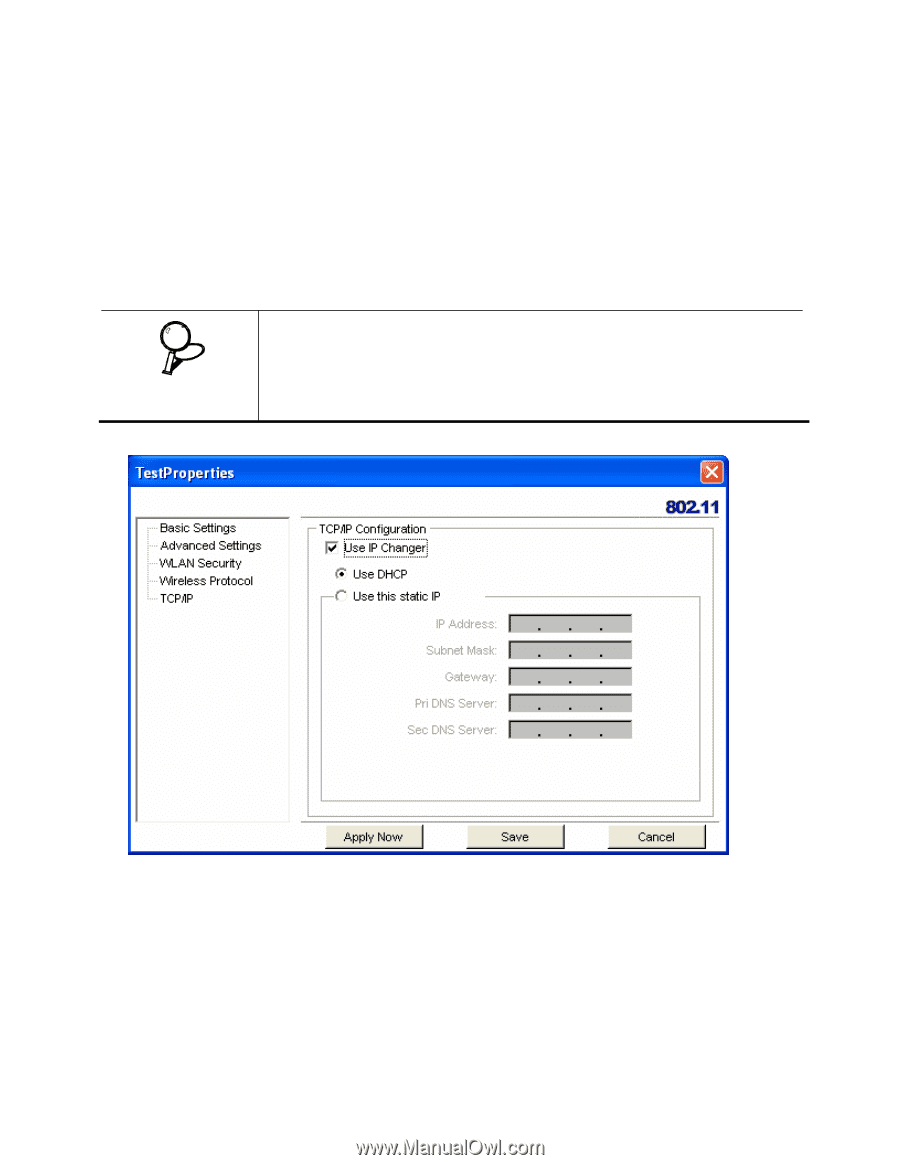
WPA/WPA2, WPA-PSK/WPA2-PSK, TCP/IP Config., Use IP Changer, Use DHCP, Use static IP below
 |
UPC - 710931502831
View all TRENDnet TEW-601PC manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 15 highlights
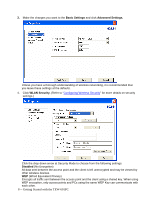
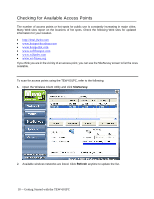
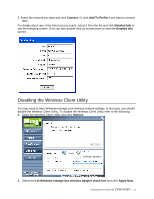
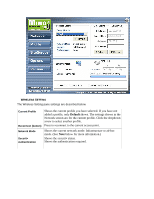
WPA/WPA2 WPA encrypts all traffic between the access point and the client using either TKIP or AES encryption. Depending on the authentication protocol selected, each client must authenticate using their own unique username, password, and security certificate. WPA-PSK/WPA2-PSK WPA-PSK or WPA2-PSK is a compromise between WPA/WPA2 and WEP. Like WEP, it uses a pre-shared key that every user of the network must have in order to send and receive data. Like WPA, it uses either TKIP or AES. IMPORTANT IT IS RECOMMEDED THAT YOU USE WPA/WPA2 OR WPA-PSK/WPA2-PSK WHENEVER POSSIBLE. WPA (WI-FI PROTECTED ACCESS) PROVIDES STRONGER ENCRYPTION THAN THE EARLIER WEP (WIRED EQUIVALENT PRIVACY) METHOD. WPA2 PROVIDES EVEN STRONGER ENCRYPTION, AUTHENTICATION AND KEY MANAGEMENT. 5. Make the changes you want and click TCP/IP Config. Select the Use IP Changer checkbox. This allows you to bypass your existing wireless TCP/ IP settings and configure TCP/IP settings for each profile. Use DHCP DHCP (Dynamic Host Configuration Protocol) automatically assign IP addresses. Check this radio button if your router is set to DHCP. Use static IP below Check this radio button if you have to enter a static IP address. Getting Started with the TEW-601PC -- 9