TRENDnet TEW-601PC User Guide - Page 36
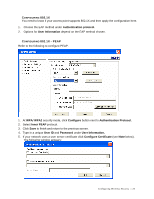
WPA applies IEEE 802.1X and Extensible Authentication Protocol EAP to authenticate wireless
 |
UPC - 710931502831
View all TRENDnet TEW-601PC manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 36 highlights
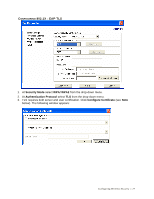
SSID The SSID (Service Set Identity) is a unique name shared among all wireless devices in a wireless network. Wireless devices must have the same SSID to communicate with each other. TEMPORAL KEY INTEGRITY PROTOCOL (TKIP) Temporal Key Integrity Protocol (TKIP) uses 128-bit keys that are dynamically generated and distributed by the authentication server. USER AUTHENTICATION WPA applies IEEE 802.1X and Extensible Authentication Protocol (EAP) to authenticate wireless clients using an external RADIUS database. If you do not have an external RADIUS server, use WPA-PSK/WPA2-PSK (WPA -Pre-Shared Key) that only requires a single (identical) password entered into each access point, wireless gateway and wireless client. As long as the passwords match, clients will be granted access to a WLAN. WEP WEP (Wired Equivalent Privacy) encryption scrambles all data packets transmitted between the TEW-601PC and the AP or other wireless stations to keep network communications private. Both the wireless stations and the access points must use the same WEP key for data encryption and decryption. WPA/WPA2 Wi-Fi Protected Access (WPA) and WPA2 (future upgrade) is a subset of the IEEE 802.11 i security specification draft. Key differences between WPA and WEP are user authentication and improved data encryption. WPA2 is a wireless security standard that defines stronger encryption, authentication and key management than WPA. 30 -- Glossary