HP 6125G HP Networking guide to hardening Comware-based devices - Page 21
Filtering BGP prefixes with prefix lists
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 21 highlights
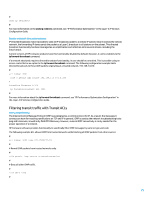
In order to prevent memory exhaustion, it is important to configure the maximum number of prefixes that is accepted on a per-peer basis. It is recommended that a limit be configured for each BGP peer. When configuring this feature using the peer route-limit command in BGP view, one argument is required: the maximum number of prefixes that are accepted before a peer is shut down. Optionally, a number from 1 to 100 can also be entered. This number represents the percentage of the maximum prefix value at which point a log message is sent. # bgp peer as-number peer route-limit # For more information, see "Limiting Prefixes Received from a Peer/Peer Group in BGP" in the Layer-3 IP Routing Configuration Guide. Filtering BGP prefixes with prefix lists Prefix lists allow a network administrator to permit or deny specific prefixes that are sent or received via BGP. Prefix lists should be used where possible to help ensure that network traffic is sent over the intended paths. Prefix lists should be applied to each eBGP peer in both inbound and outbound directions. Configured prefix lists limit the prefixes that are sent or received to those specifically permitted by a network's routing policy. If this is not feasible due to the large number of prefixes received, a prefix list should be configured to specifically block known bad prefixes. These known bad prefixes include unallocated IP address spaces and networks that are reserved for internal or testing purposes by RFC 3330. Outbound prefix lists should be configured to specifically permit only the prefixes that an organization intends to advertise. The configuration example that follows uses prefix lists to limit the routes that are learned and advertised. Specifically, only a default route is allowed in bound by prefix list BGP-PL-INBOUND, and the prefix 192.168.2.0/24 is the only route allowed to be advertised by BGP-PL-OUTBOUND. # ip ip-prefix BGP-PL-INBOUND index 5 permit 0.0.0.0 0 ip ip-prefix BGP-PL-OUTBOUND index 5 permit 192.168.2.0 24 # bgp peer ip-prefix BGP-PL-INBOUND import peer ip-prefix BGP-PL-OUTBOUND export # For more information, see "Configuring BGP Route Distribution/Reception Filtering Policies in BGP" in the Layer-3 IP Routing Configuration Guide. Filtering BGP prefixes with autonomous system path access lists BGP autonomous system (AS) path access lists allow you to filter received and advertised prefixes based on the AS path attribute of a prefix. This can be used in conjunction with prefix lists to establish a robust set of filters. The configuration example that follows uses AS path access lists to restrict inbound prefixes to those originated by the remote AS and to restrict outbound prefixes to those originated by the local autonomous system. Prefixes that are sourced from all other autonomous systems are filtered and are not installed in the routing table. # ip as-path 1 permit ^65501$ ip as-path 2 permit ^$ # bgp peer as-number 65501 21