HP 6125G HP Networking guide to hardening Comware-based devices - Page 35
Access control with MAC, Using private VLANs, Isolated VLANs
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 35 highlights
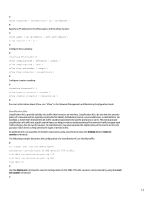
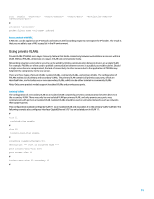
rule permit # interface packet-filter name inbound Access control with MAC A MAC ACL can be applied on an IP network and instructs the forwarding engine to not inspect the IP header. The result is that you are able to use a MAC access list in the IP environment. Using private VLANs Private VLANs (PVLANs) are a Layer 2 security feature that limits connectivity between workstations or servers within a VLAN. Without PVLANs, all devices on a Layer 2 VLAN can communicate freely. Networking situations exist where security can be aided by limiting communication between devices on a single VLAN. For example, PVLANs are often used to prohibit communication between servers in a publicly accessible subnet. Should a single server become compromised, the lack of connectivity to other servers due to the application of PVLANs may help limit the compromise to the one server. There are three types of private VLANs: isolated VLANs, community VLANs, and primary VLANs. The configuration of PVLANs makes use of primary and secondary VLANs. The primary VLAN contains all promiscuous ports, which are described later, and includes one or more secondary VLANs, which can be either isolated or community VLANs. Note: Only some product models support insolated VLANs and promiscuous ports. Isolated VLANs The configuration of a secondary VLAN as an isolated VLAN completely prevents communication between devices in the secondary VLAN. There may only be one isolated VLAN per primary VLAN, and only promiscuous ports may communicate with ports in an isolated VLAN. Isolated VLANs should be used on untrusted networks such as networks that support guests. This configuration example configures VLAN 11 as an isolated VLAN and associates it to the primary VLAN, VLAN 20. The following example also configures interface GigabitEthernet1/0/1 as an isolated port in VLAN 11: # vlan 11 isolated-vlan enable # vlan 20 isolate-user-vlan enable # interface GigabitEthernet1/0/1 description *** Port in Isolated VLAN *** port isolate-user-vlan host port access vlan 11 # isolate-user-vlan 20 secondary 11 # 35