HP 6125G HP Networking guide to hardening Comware-based devices - Page 37
Port isolation, Isolated ports
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 37 highlights
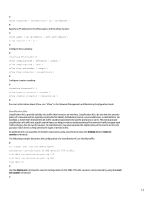
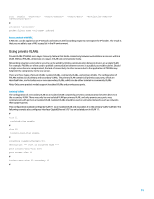
port access vlan 12 # interface GigabitEthernet1/0/12 port link-mode bridge description *** Promiscuous Port *** port isolate-user-vlan promiscuous port link-type hybrid port hybrid vlan 11 to 12 20 tagged # isolate-user-vlan 20 secondary 11 12 # When implementing PVLANs, it is important to ensure that the Layer 3 configuration in place supports the restrictions that are imposed by PVLANs and does not allow the PVLAN configuration to be subverted. Layer 3 filtering using a router ACL or firewall can prevent the subversion of the PVLAN configuration. Port isolation Port isolation is another Layer 2 security feature that limits connectivity between workstation or servers within a VLAN. Without port isolation, all devices on a Layer 2 VLAN can communicate freely. Networking situations exist where security can be aided by limiting communication between devices on a single VLAN. For example, port isolation is often used to prohibit communication between servers in a publicly accessible subnet. Should a single server become compromised, the lack of connectivity to other servers due to the application of port isolation may help limit the compromise to the one server. Port isolation includes isolated ports, uplink port, and isolation groups. HP Comware supports creating multiple isolation groups, each of which can contain multiple isolated ports and one uplink port. Layer 2 traffic is isolated among member ports in an isolation group. Note: Not all product models support uplink and isolation group functions. Isolated ports The configuration of some ports in a VLAN as isolated ports completely prevents communication between devices in the VLAN. Isolated ports should be used on untrusted networks that only access the Internet without needing to communicate with each other. The following configuration example configures all the ports of VLAN 20 as isolated ports. Interface GigabitEthernet1/0/10 and GigabitEthernet1/0/11 are in VLAN 20: # interface GigabitEthernet1/0/10 description *** Isolated Port *** port access vlan 20 port-isolate enable # interface GigabitEthernet1/0/11 description *** Isolated Port *** port access vlan 20 port-isolate enable # 37