HP 6125G HP Networking guide to hardening Comware-based devices - Page 34
Access control with VLAN QoS policy and port access control lists, Access control with VLAN QoS policy
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 34 highlights
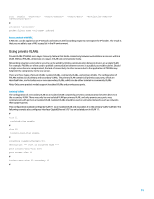
[HP] display acl 3002 Advanced ACL 3002, named ACL-SMB-CLASSIFY, 3 rules, Classification of SMB specific TCP traffic ACL's step is 5 rule 0 deny tcp destination-port eq 139 (10 times) rule 5 deny tcp destination-port eq 445 (10 times) rule 10 deny ip (205 times) # Access control with VLAN QoS policy and port access control lists VLAN access control lists (VACLs), or VLAN QoS policy and port ACLs (PACLs), provide the capability to enforce access control on non-routed traffic closer to endpoint devices than ACLs applied to routed interfaces. The sections that follow provide an overview of the features, benefits, and potential usage scenarios of VACLs and PACLs. Access control with VLAN QoS policy VACLs, or VLAN QoS policies that apply to all packets that enter the VLAN, provide the capability to enforce access control on intra-VLAN traffic. This is not possible using ACLs on routed interfaces. For example, a VLAN QoS policy may be used to prevent hosts that are contained within the same VLAN from communicating with each other, thereby reducing opportunities for local attackers or worms to exploit a host on the same network segment. In order to deny packets from using a VLAN QoS policy, you can create an ACL that matches the traffic and, in the VLAN QoS policy, set the action to drop. Once a VLAN QoS policy is configured, all packets that enter the LAN are sequentially evaluated against the configured VLAN QoS policy. The following example utilizes an extended named access list that illustrates the configuration of this feature: # acl number 3003 name rule permit # [HP]traffic behavior [HP-behavior-b1] [HP]traffic classifier [HP-classifier-b1] if-match [HP]qos policy [HP-qospolicy-c1]classifier behavior # [HP]qos vlan-policy vlan 100 inbound # Access control with PACLs PACLs can only be applied to the inbound direction on Layer 2 physical interfaces of a switch. The syntax for creating PACLs, which take precedence over VLAN QoS policies and router ACLs, is the same as it is for router ACLs. An ACL applied to a Layer-2 interface is referred to as a PACL. Configuration involves creating an IPv4, IPv6, or MAC ACL and applying it to the Layer 2 interface. The following example utilizes an extended ACL to illustrate the configuration of this feature: # acl number 3003 name 34