HP 6125G HP Networking guide to hardening Comware-based devices - Page 22
Securing Interior Gateway Protocols, Routing protocol authentication and verification with MD5
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 22 highlights
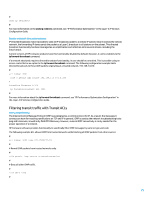
peer as-path-acl 1 import peer as-path-acl 2 export # Securing Interior Gateway Protocols The ability of a network to properly forward traffic and recover from topology changes or faults is dependent on an accurate view of the topology. Running an Interior Gateway Protocol (IGP) can often provide this view. By default, IGPs are dynamic and discover additional routers that communicate with the particular IGP in use. IGPs also discover routes that can be used during a network link failure. These subsections provide an overview of the most important IGP security features. Recommendations and examples that cover Routing Information Protocol Version 2 (RIPv2), open shortest path first (OSPF), and Intermediate System to Intermediate System (IS-IS) are provided when appropriate. Routing protocol authentication and verification with MD5 Failure to secure the exchange of routing information allows an attacker to introduce false routing information into the network. By using password authentication with routing protocols between routers, you can aid the security of the network. However, because this authentication is sent as cleartext, it can be simple for an attacker to subvert this security control. By adding MD5 hash capabilities to the authentication process, routing updates no longer contain cleartext passwords, and the entire content of the routing update is more resistant to tampering. However, MD5 authentication is still susceptible to brute force and dictionary attacks if weak passwords are chosen. You are advised to use passwords with sufficient randomization. Because MD5 authentication is much more secure when compared to password authentication, these examples are specific to MD5 authentication. An example of MD5 router authentication configuration for RIPv2 follows. RIPv1 does not support authentication. # interface rip authentication-mode md5 rfc2543 # For more information, see "Configuring RIPv2 Message Authentication in RIP" in the Layer-3 IP Routing Configuration Guide. Following is an example configuration for OSPF router authentication using MD5: # interface ospf authentication-mode md5 # ospf area 0 authentication-mode md5 # For more information, see "Configuring OSPF Authentication in OSPF" in the Layer-3 IP Routing Configuration Guide. Following is an example configuration for IS-IS router authentication using MD5: # interface isis authentication-mode md5 # isis 22