HP 6125G HP Networking guide to hardening Comware-based devices - Page 33
Classification ACLs, Network Management and Monitoring Configuration Guide
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 33 highlights
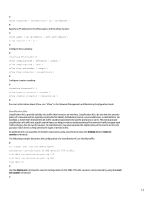
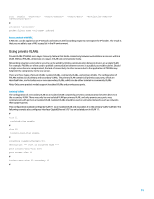
# sflow collector < collector-id > ip < ip-address > # Specify an IP address for the sFlow agent, and the sFlow version. # sflow agent { ip ip-address | ipv6 ipv6-address } sflow version { 4 | 5 } # Configure flow sampling: # interface Ethernet0/1/0 sflow sampling-mode { determine | random } sflow sampling-rate < rate > sflow flow max-header < length > sflow flow collector < collector-id > # Configure counter sampling: # interface Ethernet0/1/1 sflow counter interval < seconds > sflow counter collector < collector-id > # For more information about sFlow, see "sFlow" in the Network Management and Monitoring Configuration Guide. Classification ACLs Classification ACLs provide visibility into traffic that traverses an interface. Classification ACLs do not alter the security policy of a network and are typically constructed to classify individual protocols, source addresses, or destinations. For example, a match item that permits all traffic could be separated into specific protocols or ports. This more granular classification of traffic into specific match items can help provide an understanding of the network traffic because each traffic category has its own hit counter. An administrator may also separate the implicit deny at the end of an ACL into granular match items to help identify the types of denied traffic. An administrator can expedite an incident response by using classification ACLs with display acl and reset acl counter commands. The following example illustrates the configuration of a classification ACL to identify traffic: # acl number 3002 name ACL-SMB-CLASSIFY description Classification of SMB specific TCP traffic rule deny tcp destination-port eq 139 rule deny tcp destination-port eq 445 rule deny ip # Use the display acl command to view the configuration of ACL 3002. (The ACL counters can be cleared by using the reset acl counter command.) # 33