HP 6125G HP Networking guide to hardening Comware-based devices - Page 26
Filtering IP fragments, Anti-spoofing protections, URPF, IP source guard
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 26 highlights
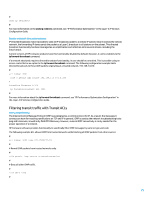
Filtering IP fragments As detailed previously in the "Limiting access to the network with infrastructure ACLs" section of this document, the filtering of fragmented IP packets can pose a challenge to security devices. Because of the nonintuitive nature of fragment handling, IP fragments are often inadvertently permitted by ACLs. Fragmentation is also often used in attempts to evade detection by intrusion detection systems. It is for these reasons that IP fragments are often used in attacks and should be explicitly filtered at the top of any configured traffic ACLs. The example ACL that follows includes comprehensive filtering of IP fragments. The functionality illustrated in this example must be used in conjunction with the functionality of the previous examples: # acl number 3000 name ACL-TRANSIT-IN # # Deny IP fragments using protocol-specific ACEs to aid in classification of attack traffic. # rule deny tcp fragment rule deny udp fragment rule deny icmp fragment rule deny ip fragment # Anti-spoofing protections Many attacks utilize source IP address spoofing to be effective or to conceal the true source of an attack and hinder accurate traceback. HP Comware provides Unicast Reverse Path Forwarding (URPF) and IP Source Guard (IPSG) to deter attacks that rely on source IP address spoofing. In addition, ACLs and null routing are often deployed as a manual means of spoofing prevention. IP Source Guard is effective at reducing spoofing for networks that are under direct administrative control by performing switch port, MAC address, and source address verification. URPF provides source network verification and can reduce spoofed attacks from networks that are not under direct administrative control. Port security can be used in order to validate MAC addresses at the access layer. ARP detection mitigates attack vectors that utilize ARP poisoning on local segments. URPF URPF enables a device to verify that the source address of a forwarded packet can be reached through the interface that received the packet. You must not rely on URPF as the only protection against spoofing. Spoofed packets could enter the network through a URPF-enabled interface if an appropriate return route to the source IP address exists. URPF can be configured in one of two modes: loose or strict. In cases where there is asymmetric routing, loose mode configuration is preferred because strict mode is known to drop packets in these situations. The following example illustrates configuration of this feature: # interface Ethernet0/1/0 ip urpf loose # URPF can be configured globally or on the interface, depending on the device model. For more information about the configuration and use of URPF, see "URPF" in the Security Configuration Guide. IP source guard IP source guard is an effective means of spoofing prevention in Layer 2 access mode. 26