HP 6125G HP Networking guide to hardening Comware-based devices - Page 36
Community VLANs, Promiscuous ports, ports. Promiscuous ports can
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 36 highlights
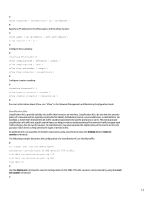
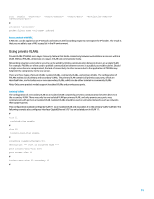
Community VLANs A secondary VLAN that is configured as a community VLAN allows communication among members of the VLAN as well as with any promiscuous ports in the primary VLAN. However, no communication is possible between any two community VLANs or from a community VLAN to an isolated VLAN. Community VLANs must be used to group servers that need connectivity with one another, but where connectivity to all other devices in the VLAN is not required. This scenario is common in a publicly accessible network or anywhere that servers provide content to untrusted clients. The following example configures a single community VLAN and configures switch port GigabitEthernet1/0/2 as a member of that VLAN. The community VLAN, VLAN 12, is a secondary VLAN to primary VLAN 20. Note: A secondary VLAN is considered a community VLAN by default. # vlan 12 # vlan 20 isolate-user-vlan enable # interface GigabitEthernet1/0/2 description *** Port in Community VLAN *** port isolate-user-vlan host port access vlan 12 # isolate-user-vlan 20 secondary 12 # Promiscuous ports Switch ports that are placed into the primary VLAN are known as promiscuous ports. Promiscuous ports can communicate with all other ports in the primary and secondary VLANs. Router or firewall interfaces are the most common devices found on these VLANs. The following configuration example combines the previous isolated and community VLAN examples and adds the configuration of interface GigabitEthernet1/0/12 as a promiscuous port: # vlan 11 isolated-vlan enable # vlan 12 # vlan 20 isolate-user-vlan enable # interface GigabitEthernet1/0/1 description *** Port in Isolated VLAN *** port isolate-user-vlan host port access vlan 11 # interface GigabitEthernet1/0/2 description *** Port in Community VLAN *** port isolate-user-vlan host 36