HP 6125G HP Networking guide to hardening Comware-based devices - Page 24
Securing Virtual Router Redundancy Protocol, Data plane, General data plane hardening
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 24 highlights
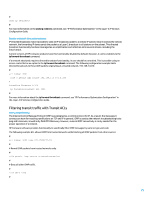
ip ip-prefix index 10 permit # ospf area filter ip-prefix import # For more information on OSPF Area Border Router (ABR) Type 3 link-state advertisements filtering, see "Configuring ABR Type-3 LSA Filtering in OSPF" in the Layer-3 IP Routing Configuration Guide. Securing Virtual Router Redundancy Protocol Virtual Router Redundancy Protocol (VRRP) provides resiliency and redundancy for devices that are acting as default gateways. By default, VRRP communicates using unauthenticated communication. This kind of communication can allow an attacker to pose as a fake device to assume a network's default gateway role. This takeover would allow an attacker to perform a man-in-the-middle attack and intercept all user traffic that exits the network. In order to prevent this type of attack, VRRP supported by HP Comware software includes an authentication capability using either MD5 or plain text. Because of the threat posed by unauthenticated VRRPs, it is recommended that instances of these protocols use MD5 authentication. The following configuration example demonstrates the use of VRRP MD5 authentication: # interface Ethernet0/1/0 vrrp vrid virtual-router-id authentication-mode md5 # For more information, see "VRRP" in the High Availability Configuration Guide. Data plane Although the data plane is responsible for moving data from source to destination, within the context of security, the data plane is the least important of the three planes. It is for this reason that when you are securing a network device, it is important to protect the management and control planes in preference over the data plane. However, within the data plane itself, there are many features and configuration options that can help secure traffic. The sections that follow detail these features and options so that you can more easily secure your network. General data plane hardening The vast majority of data plane traffic flows across the network as determined by the network's routing configuration. However, IP network functionality exists to alter the path of packets across the network. Features such as IP Options, specifically the source routing option, form a security challenge in today's networks. The use of Transit ACLs is also relevant to the hardening of the data plane. For more information, see the "Filtering transit traffic with Transit ACLs" section of this document. Disable ICMP redirects ICMP redirects are used to inform a network device of a better path to an IP destination. In some situations, it may be possible for an attacker to cause the device to send many ICMP redirect messages, resulting in an elevated CPU load. For this reason, it is recommended that the transmission of ICMP redirects be disabled. By default, HP Comware software does not send a redirect if it receives a packet that must be routed through the interface it was received from. ICMP redirects are disabled using the undo ip redirects command in system view, as shown in the following example configuration: 24