HP 6125G HP Networking guide to hardening Comware-based devices - Page 29
ARP Detection, Anti-spoofing ACLs
 |
View all HP 6125G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 29 highlights
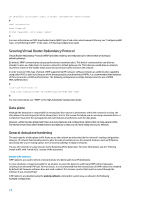
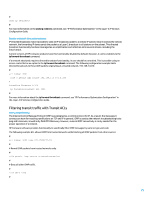
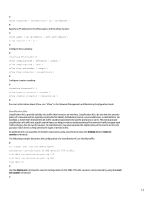
ARP Detection ARP Detection can be utilized to mitigate ARP poisoning attacks on local segments. An ARP poisoning attack is a method in which an attacker sends falsified ARP information to a local segment. This information is designed to corrupt the ARP cache of other devices. Often an attacker uses ARP poisoning in order to perform a man-in-the-middle attack. ARP Detection intercepts and validates the IP-to-MAC address relationship of all ARP packets on untrusted ports. In DHCP environments, ARP Detection utilizes the data that is generated by the DHCP snooping feature. In 802.1X environments, ARP Detection can use the user data generated by the 802.1x feature. ARP packets that are received on trusted interfaces are not validated and invalid packets on untrusted interfaces are discarded. In non-DHCP or non-802.1X environments, the configuration of static client entries is required. Even if in DHCP environments, there may be some users such as servers or printers that use manually configured IP addresses. In such environments, static client entries are also the requisites when enabling ARP Detection. The following command enables DHCP snooping: # dhcp-snooping # Once DHCP snooping has been enabled, the following commands enable ARP Detection: # vlan 1 arp detection enable # In non-DHCP or non-802.1x environments, static client entries on a port are required to enable ARP Detection. The following example demonstrates the basic configuration of a static client entry: # interface Ethernet0/4/0 user-bind ip-address mac-address vlan # For more information on how to configure ARP Detection, see "ARP Attack Protection" in the Security Configuration Guide. Anti-spoofing ACLs Manually configured ACLs can provide static anti-spoofing protection against attacks that utilize known unused and untrusted address space. Commonly, these anti-spoofing ACLs are applied to ingress traffic at network boundaries as a component of a larger ACL. Anti-spoofing ACLs require regular monitoring because they can frequently change. Spoofing can be reduced in traffic originating from the local network by applying outbound ACLs that limit the traffic to valid local addresses. The following example demonstrates how ACLs can be used to limit IP spoofing. This ACL is applied in bound on the desired interface: # acl number 3001 name ACL-ANTISPOOF-IN rule deny ip source 10.0.0.0 0.255.255.255 rule deny ip source 192.168.0.0 0.0.255.255 # # For Switch, port ACL command is "packet-filter" interface packet-filter name ACL-ANTISPOOF-IN inbound # For Router, port ACL command is "firewall packet-filter" interface 29