HP StorageWorks 8/80 HP StorageWorks Fabric OS 6.2.0g release notes (5697-0035 - Page 48
High Availability Cluster HAC/Data Encryption Key DEK cluster
 |
View all HP StorageWorks 8/80 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 48 highlights
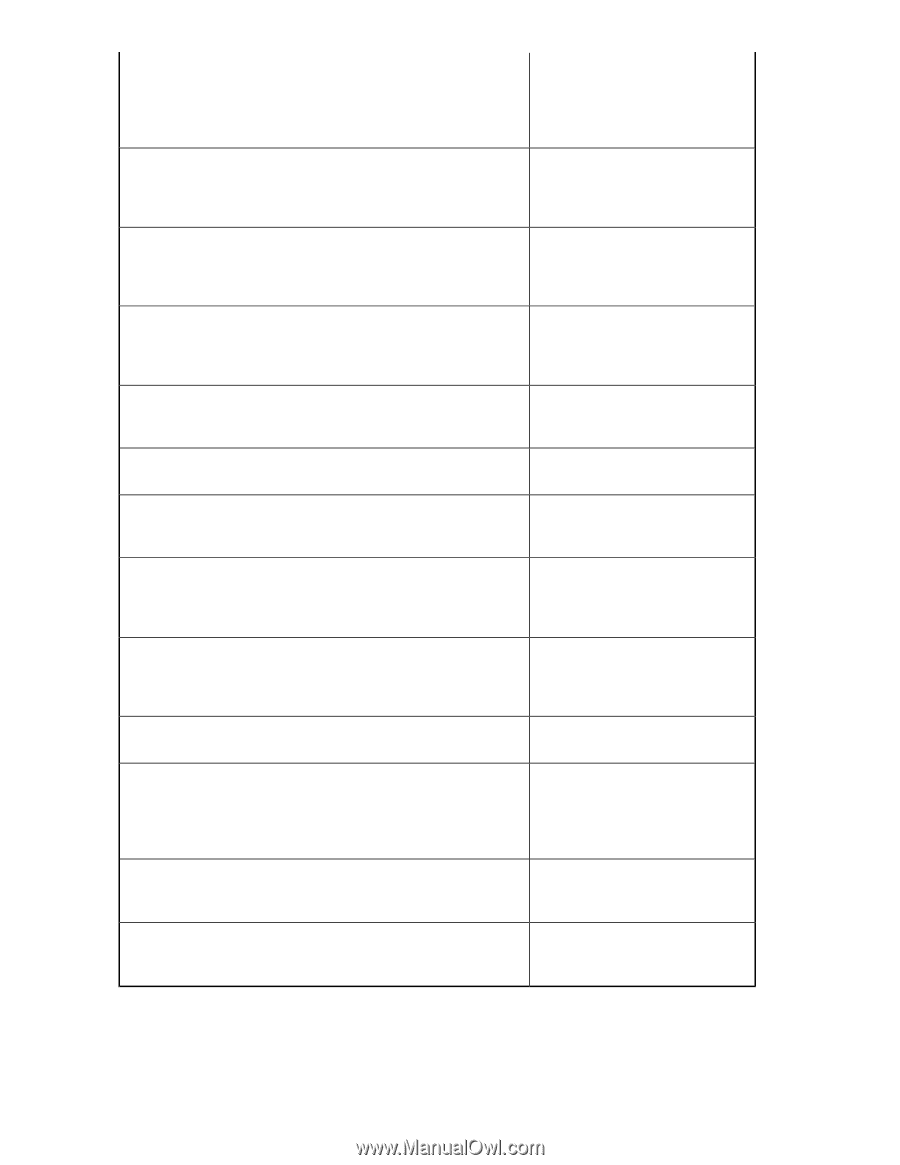
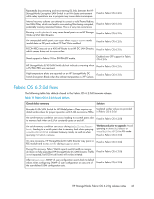
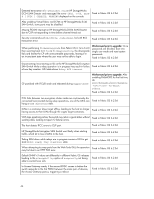
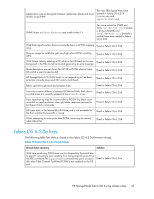
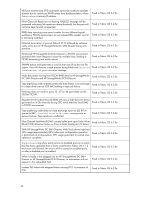
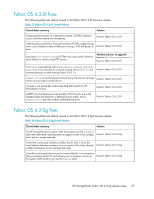
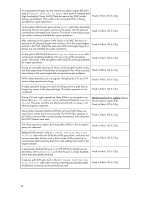
An encrypted LUN goes into the internal encryption engine (EE) LUN state (Disabled (key not in sync)) as a result of rekeying and High Availability Cluster (HAC)/Data Encryption Key (DEK) cluster failover and failback. This results in the encrypted LUN not being available for crypto operations. Fixed in Fabric OS 6.2.0g An Encryption SAN Switch goes into the faulty state after alternately rebooting the two encryption switches in the group with the physical connectivity to the targets and initiators. This results in the faulty encryption switch not being available for crypto operations. Fixed in Fabric OS 6.2.0g After rebooting an Encryption SAN Switch of an HAC that has connectivity to the physical targets and initiators, all of the crypto targets are lost in the HAC. LUNs that were part of the lost crypto target containers are not available for crypto operations. Fixed in Fabric OS 6.2.0g An Encryption SAN Switch shows Encryption Engine busy when continuously disabling/enabling I/O sync ports of the encryption switch. This results in the encryption switch and EE not being available for crypto operations. Fixed in Fabric OS 6.2.0g During an overnight stress test of rekey and ISL disable/enable cycles, one host experienced write failures to encrypted LUNs, while a second Fixed in Fabric OS 6.2.0g host writing to the same targets did not experience any problems. While rekey operations are in progress, disrupting the I/O sync link Fixed in Fabric OS 6.2.0g causes rekey operations to hang. A rekey operation hangs as a result of failing over to a path that no longer has access to the physical target. The rekey operation is not completed. Fixed in Fabric OS 6.2.0g During I/O and crypto operations, three LUNs in an encryption container show Key ID Unavailable, and one LUN shows inquiry failed. However, all LUNs are fully functional with no issues in all other encryption containers. Workaround prior to update: Reboot the Encryption engine (EE). Fixed in Fabric OS 6.2.0g Mixing Fibre Channel FastWrite (FCFW) and non-FCFW flows can cause dcam entries to be set incorrectly. The FCFW flow appears to fail without any port-filter counters being incremented, indicating that the FCFW frames were seen. Fixed in Fabric OS 6.2.0g The rekey operation restarts, but hangs after all EEs in the encryption Fixed in Fabric OS 6.2.0g group are rebooted. Rekeyed LUNs remain in the Not Ready (Getting key from archive) state when the SKM (key vault) goes down, and does not recover even after the key vault is back online. LUNs cannot be recovered even after removing them from and adding them back to the target container. Fixed in Fabric OS 6.2.0g A persistently disabled GE port on an HP MP Router blade loses its persistency after hafailover, such that the port is simply disabled, rather than persistently disabled. Fixed in Fabric OS 6.2.0g A passive path LUN gets stuck in the Not Ready (Getting key from archive) state when running a test that periodically breaks the Ethernet connection to the primary key vault. Fixed in Fabric OS 6.2.0g 48