ZyAIR G-300 User’s Guide
Index
CC
Index
A
About
.....................................................
2-20
Accessing the ZyAIR Utility
.....................
1-2
AdHoc Channel
.....................................
2-11
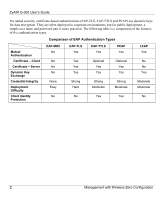
authentication
........................................
2-19
authentication mode
..............................
2-14
Authentication Mode
................................
2-6
Open
....................................................
2-6
Shared
..................................................
2-6
automatically key generation
.................
2-15
B
Basic Service Set
...........................
See
BSS
BSS
..........................................................
2-2
C
CA
...............................................................
Y
certificate
...............................................
2-17
server
.................................................
2-18
user
....................................................
2-17
Certificate Authority
..........................
See
CA
Certificate Authority (CA)
.......................
2-18
Certificate screen, the
............................
2-16
Communication Problem
.........................
4-1
Ad-hoc(IBSS)
.......................................
4-2
Infrastructure
........................................
4-1
Configuration utility version
...................
2-21
Connecting to a Network
.......................
2-20
Copyright
.....................................................
ii
Disclaimer
................................................
ii
Trademarks
..............................................
ii
CTS (Clear to Send
..........................
2-4, 2-5
Customer Support
.....................................
vii
D
Data encryption
........................................
2-6
Disable Windows XP Wireless Support... 1-1
E
EAP Authentication
MD5
.........................................................
Y
PEAP
.......................................................
Y
TLS
..........................................................
Y
TTLS
........................................................
Y
EAP type
................................................
2-15
encryption
..............................................
2-19
Encryption
................................................
2-7
encryption method
.................................
2-14
ESS
..........................................................
2-2
Extended Service Set
.....................
See
ESS
F
Federal Communications Commission
(FCC) Interference Statement
..................
v
Frag Threshold
.......................................
2-13
Fragmentation Threshold
.........................
2-4
Frequency domain
.................................
2-21
G
Graphics Icons Key
...................................
xiii
H
Hidden node
.............................................
2-4
I
IBSS
.........................................................
2-1