Dell PowerConnect W Clearpass 100 Software Cisco WLC Integration Guide - Page 3
Introduction
 |
View all Dell PowerConnect W Clearpass 100 Software manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 3 highlights
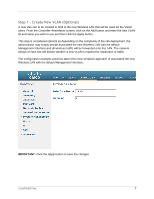
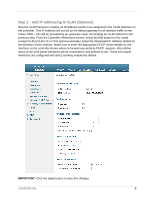
Introduction This document outlines the configuration process on both the Cisco Wireless LAN Controller (WLC) and the Amigopod appliance to create a fully integrated Visitor Management solution. The solution leverages the captive portal functionality built into the Cisco WLC software image. The captive portal functionality allows a wireless client to authenticate using a web-based portal. Captive portals are typically used in public access wireless hotspots or for hotel in-room Internet access. After a client associates to the wireless network, their device is assigned an IP address. The client must start a web browser and pass an authentication check before access to the network is granted. Captive portal authentication is the simplest form of authentication to use and requires no software installation or configuration on the client. The username/password exchange is encrypted using standard SSL encryption. However, portal authentication does not provide any form of encryption beyond the authentication process; to ensure privacy of client data, some form of link-layer encryption (such as WEP or WPA-PSK) should be used when sensitive data will be sent over the wireless network. Amigopod extends the standard Cisco WLC captive portal functionality by providing many advanced features such as a fully branded user interface, SMS integration for delivery of receipts, bulk upload of visitors for conference management, self provisioning of users for public space environments to name a few. Test Environment The test environment referenced throughout this integration guide is based on an Cisco WLC 4402 controller. Although this low end hardware platform has been used, the testing and therefore this procedure is valid for all hardware variants from Cisco in its WLC range including the WiSM blade that installs as a module in the Catalyst 6500 switching platform. The WLC range in based on the Cisco acquisition of Airespace and therefore this integration guide is valid for any solution based on the Airespace technology. Other Cisco wireless reference designs such as Autonomous IOS Access Points and the preceding WLSM architecture do not natively support the required Captive Portal functionality and therefore are not covered in this Integration Guide. CONFIDENTIAL 3