Dell PowerConnect W-Series FIPS Dell PowerConnect W-600 Controller Series Secu - Page 20
Service, Description, Input, Output, CSP Access, Crypto-Officer Services
 |
View all Dell PowerConnect W-Series FIPS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 20 highlights
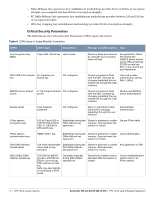
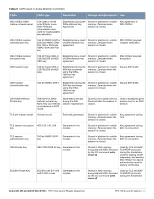
Table 3 Crypto-Officer Services Service Description Input Output CSP Access Configuring Network Management Create management Users and set their password and privilege level; configure the SNMP agent Commands and configuration data Status of commands and configuration data Crypto Officer's password for CLI (read/write access) Configuring the module Platform Define the platform subsystem firmware of the module by entering Bootrom Monitor Mode, File System, fault report, message logging, and other platform related commands Commands and configuration data Status of commands and configuration data None Configuring Hardware Controllers Define synchronization features Commands and for module configuration data Status of commands and configuration data None Configuring the Set IP functionality Internet Protocol Commands and configuration data Status of commands and configuration data None Configuring Quality Configure QOS values for module Commands and of Service (QoS) configuration data Status of commands and configuration data None Configuring the VPN Configure Public Key Infrastructure (PKI); configure the Internet Key Exchange (IKEv1/ IKEv2) Security Protocol; configure the IPSec protocol Commands and configuration data Status of commands and configuration data RSA and ECDSA keys pair (read/write access), Preshared key (read/write access) Configuring DHCP Configure DHCP on module Commands and configuration data Status of commands and configuration data None Configuring Security Define security features for module, including Access List, AAA, and firewall functionality Commands and configuration data Status of commands and configuration data AAA User password (read/ write access), RADIUS password (read/ write access) HTTPS over TLS Secure browser connection over Transport Layer Security acting as a Crypto Officer service (web management interface) TLS inputs, commands, and data TLS outputs, status, and data RSA key pair for TLS; TLS Session Key IPSec tunnel Provided authenticated/ establishment for encrypted channel to RADIUS RADIUS protection server IKEv1/IKEv2 inputs and data; IPSec inputs, commands, and data IKEv1/IKEv2 outputs, status, and data; IPSec outputs, status, and data Preshared key/RSA private key for IKEv1/IKEv2 (read access), Diffie-Hellman and Elliptic curve Diffie-Hellman key pair for IKEv1/IKEv2 (read/write access), Session keys for IPSec (read/write access) Self-test Run Power On Self-Tests and Conditional Tests None Error messages logged if a failure occurs None Configuring Configure bypass operation on Bypass Operation the module Commands and configuration data Status of commands and configuration data None 18 | FIPS 140-2 Level 2 Features Aruba 620, 650 and Dell W-620, W-650 | FIPS 140-2 Level 2 Release Supplement