Dell PowerConnect W-Series FIPS Dell PowerConnect W-600 Controller Series Secu - Page 26
CSPs type, Generation, Storage and Zeroization, Seed ANSI X9.31 RNG
 |
View all Dell PowerConnect W-Series FIPS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 26 highlights
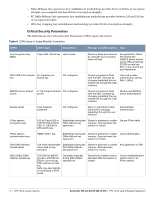
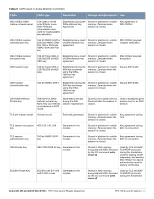
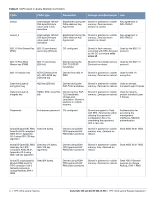
Table 6 CSPs Used in Aruba Mobility Controllers CSPs CSPs type Generation Storage and Zeroization Use skeyid Intermediate 160-bit/ 256-byte/384-byte value used in key derivation Established during the Stored in plaintext in volatile Key agreement in Diffie-Hellman Key memory. Zeroized when IKEv1/IKEv2 Agreement session is closed. skeyid_d Intermediate 160-bit/ 256-byte/384-byte value used in key derivation Established during the Stored in plaintext in volatile Key agreement in Diffie-Hellman Key memory. Zeroized when IKEv1/IKEv2 Agreement session is closed. 802.11i Pre-Shared Key 802.11i pre-shared (PSK) secret key (256-bit) CO configured Stored in flash memory encrypted with KEK. Zeroized by the CO command write erase all. Used by the 802.11i protocol 802.11i Pair-Wise Master key (PMK) 802.11i secret key (256-bit) Derived during the EAP-TLS/PEAP handshake Stored in the volatile memory. Used by the 802.11i Zeroized on reboot. protocol 802.11i session key AES-CCM key (128 bit), AES-GCM key (128/256-bit) Derived from 802.11 Stored in plaintext in volatile Used for 802.11i PMK memory. Zeroized on reboot. encryption Data link (Layer 2) encryption key AES key (256 bit) Derived during the Stored in plaintext in volatile Used to encrypt EAP-TLS handshake memory. Zeroized on reboot. tunneled Layer 2 frames Data link (Layer 2) integrity key HMAC-SHA1 key (160bit) Derived during EAPTLS handshake storage and zeroization: Stored in plaintext in volatile memory Stored in plaintext in volatile Used to integritymemory. Zeroized on reboot. protect tunneled Layer 2 frames Passwords 6-character password CO configured Stored encrypted in Flash with KEK. Zeroized by either deleting the password configuration file or by overwriting the password with a new one. Authentication for accessing the management interfaces, RADIUS authentication ArubaOS OpenSSL RNG Seed for FIPS compliant ANSI X9.31, Appendix A2.4 using AES-128 key algorithm Seed (16 bytes) Derived using NONFIPS approved HW RNG (/dev/urandom) Stored in plaintext in volatile Seed ANSI X9.31 RNG memory only. Zeroized on reboot. ArubaOS OpenSSL RNG Seed key for FIPS compliant ANSI X9.31, Appendix A2.4 using AES-128 key algorithm Seed key (16 bytes, AES-128 key algorithm) Derived using NONFIPS approved HW RNG (/dev/urandom) Stored in plaintext in volatile Seed ANSI X9.31 RNG memory only. Zeroized on reboot. ArubaOS cryptographic Module RNG seed for FIPS compliant 186-2 General purpose (xchange Notice); SHA-1 RNG Seed (64 bytes) Derived using NONFIPS approved HW RNG (/dev/urandom) Stored in plaintext in volatile Seed 186-2 General memory. Zeroized on reboot. purpose (x-change Notice); SHA-1 RNG 24 | FIPS 140-2 Level 2 Features Aruba 620, 650 and Dell W-620, W-650 | FIPS 140-2 Level 2 Release Supplement