Dell PowerConnect W-Series FIPS Dell PowerConnect W-600 Controller Series Secu - Page 21
User Role, Table 3 - certification
 |
View all Dell PowerConnect W-Series FIPS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 21 highlights
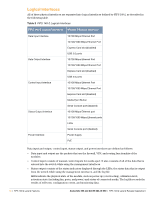
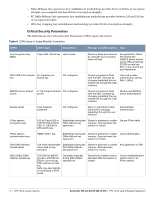
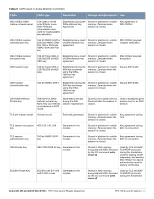
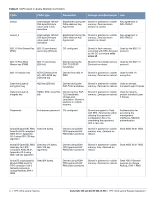
Table 3 Crypto-Officer Services Service Description Input Output CSP Access Updating Firmware Updating firmware on the module Commands and configuration data Status of commands and configuration data None Configuring OCSP Configuring OCSP responder Responder functionality OCSP inputs, OCSP outputs, commands, and data status, and data RSA/ECDSA key pair for signing OCSP responses Configuring Control Plane Security (CPSec) Configuring Control Plane Security mode to protect communication with APs using IPSec and issue self signed certificates to APs Commands and configuration data, IKEv1/IKEv2 inputs and data; IPSec inputs, commands, and data Status of commands, IKEv1/ IKEv2 outputs, status, and data; IPSec outputs, status, and data and configuration data, self signed certificates RSA private key for IKEv1/ IKEv2 and certificate signing (read access), Diffie-Hellman key pair for IKEv1/IKEv2 (read/write access), Session keys for IPSec (read/write access) User Role The User role can access the switch's IPSec and IKEv1/IKEv2 services. Service descriptions and inputs/ outputs are listed in the following table: Table 4 User Service Service Description Input Output CSP Access IKEv1/IKEv2-IPSec Access the module's IPSec services in order to secure network traffic HTTPS over TLS EAP-TLS termination Access the module's TLS services in order to secure network traffic Provide EAP-TLS termination 802.11i Shared Key Mode Access the module's 802.11i services in order to secure network traffic 802.11i with EAP- Access the module's 802.11i TLS services in order to secure network traffic IPSec inputs, IPSec outputs, commands, and data status, and data TLS inputs, commands, TLS outputs, and data status, and data RSA and ECDSA key pair for IKEv1/IKEv2 (read access); Diffie-Hellman and Elliptic curve Diffie-Hellman key pair for IKEv1/IKEv2 (read and write access); pre-shared keys for IKEv1/IKEv2 (read access) RSA key pair for TLS; TLS Session Key EAP-TLS inputs, commands and data 802.11i inputs, commands and data 802.11i inputs, commands and data EAP-TLS outputs, status and data EAP-TLS RSA private key (read) EAP-TLS ECDSA private key (read) 802.11i outputs, status and data 802.11i Pre-Shared Key (read) 802.11i Session key (read/ write) 802.11i outputs, status, and data EAP-TLS RSA private key (read) EAP-TLS ECDSA private key (read) 802.11i Pair-Wise Master Key (read/ write) 802.11i Session key (read/write) Aruba 620, 650 and Dell W-620, W-650 | FIPS 140-2 Level 2 Release Supplement FIPS 140-2 Level 2 Features | 19