HP 6120XG HP ProCurve Series 6120 Blade Switches Access Security Guide - Page 150
Configuring the TACACS+ Server for Single Login, In the User Setup
 |
View all HP 6120XG manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 150 highlights
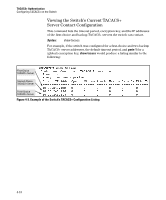
TACACS+ Authentication Configuring TACACS+ on the Switch Name enable login local - or tacacs local - or none num-attempts Default n/a Range n/a privilege-mode n/a disabled local n/a none n/a 3 1 - 10 Function Specifies the Manager (read/write) privilege level for the access method being configured. login: Specifies the Operator (read-only) privilege level for the access method being configured. The privilege-mode option enables TACACS+ for a single login. The authorized privilege level (Operator or Manager) is returned to the switch by the TACACS+ server. Specifies the primary method of authentication for the access method being configured. local: Use the username/password pair configured locally in the switch for the privilege level being configured tacacs: Use a TACACS+ server. Specifies the secondary (backup) type of authentication being configured. local: The username/password pair configured locally in the switch for the privilege level being configured none: No secondary type of authentication for the specified method/privilege path. (Available only if the primary method of authentication for the access being configured is local.) Note: If you do not specify this parameter in the command line, the switch automatically assigns the secondary method as follows: • If the primary method is tacacs, the only secondary method is local. • If the primary method is local, the default secondary method is none. In a given session, specifies how many tries at entering the correct username/password pair are allowed before access is denied and the session terminated. Configuring the TACACS+ Server for Single Login In order for the single login feature to work correctly, you need to check some entries in the User Setup on the TACACS+ server. In the User Setup, scroll to the Advanced TACACS+ Settings section. Make sure the radio button for "Max Privilege for any AAA Client" is checked and the level is set to 15, as shown in Figure 4-4. Privileges are represented by the numbers 0 through 15, with zero allowing only Operator privileges (and requiring two logins) and 15 representing root privileges. The root privilege level is the only level that will allow Manager level access on the switch. 4-13