HP XP20000/XP24000 HP StorageWorks XP24000/XP20000 Audit Log Reference Guide ( - Page 254
Audit Log Information about the Key Used for the Encryption License Key
 |
View all HP XP20000/XP24000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 254 highlights
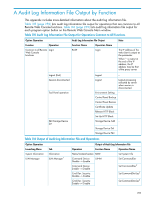
45 Audit Log Information about the Key Used for the Encryption License Key This chapter provides audit log information about the key used for data encryption. • "Encryption (ENC) Function - Create Enc. Key Operation" (page 254) • "Encryption (ENC) Function - Enc. Key Backup Operation" (page 254) • "Encryption (ENC) Function - Enc. Key Restore Operation" (page 254) • "Encryption (ENC) Function - PG Enc. Set Operation" (page 255) • "Install Function - Set Encryption Key Operation" (page 255) Encryption (ENC) Function - Create Enc. Key Operation ,xx,YYYY/MM/DD,HH:MM:SS.xxx, 00:00,[ENC],Create Enc. Key,,Normal end,,,Seq.=xxxxx [ENC] ENC function Create Enc. Key Create Encryption Key operation Normal end The operation has ended normally. Seq.=xxxxxx Log information serial number (0000000000 to 4294967295) Encryption (ENC) Function - Enc. Key Backup Operation user-name,xx,YYYY/MM/DD,HH:MM:SS.xxx, 00:00,[ENC],Enc. Key Backup,,Normal end,,,Seq.=xxxxx [ENC] ENC function Enc. Key Backup Encryption Key Backup operation Normal end The operation has ended normally. Seq.=xxxxxx Log information serial number (0000000000 to 4294967295) Encryption (ENC) Function - Enc. Key Restore Operation user-name,xx,YYYY/MM/DD,HH:MM:SS.xxx, 00:00,[ENC],Enc. Key Restore,,Normal end,,,Seq.=xxxxx [ENC] ENC function Enc. Key Restore Encryption Key Restore operation Normal end The operation has ended normally. Seq.=xxxxxx Log information serial number (0000000000 to 4294967295) 254 Audit Log Information about the Key Used for the Encryption License Key