TP-Link TL-R480T User Guide - Page 50
TL-R480T, Region, Scan Attack Defence, IP Scan, destination IP addresses
 |
UPC - 696726480020
View all TP-Link TL-R480T manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 50 highlights
TL-R480T SMB Broadband Router User Guide Figure 4-37 ¾ Region - This option used to select the specifically area from which the packets will be monitored by the next settings. ¾ Scan Attack Defence • IP Scan: During the specific time, if a computer (identified by a particular source IP address) transmits packets to at least ten different computers (identified by different destination IP addresses), then the source IP address will be deemed to make IP Attacks. And the Router will start up the blocking function immediately. 44
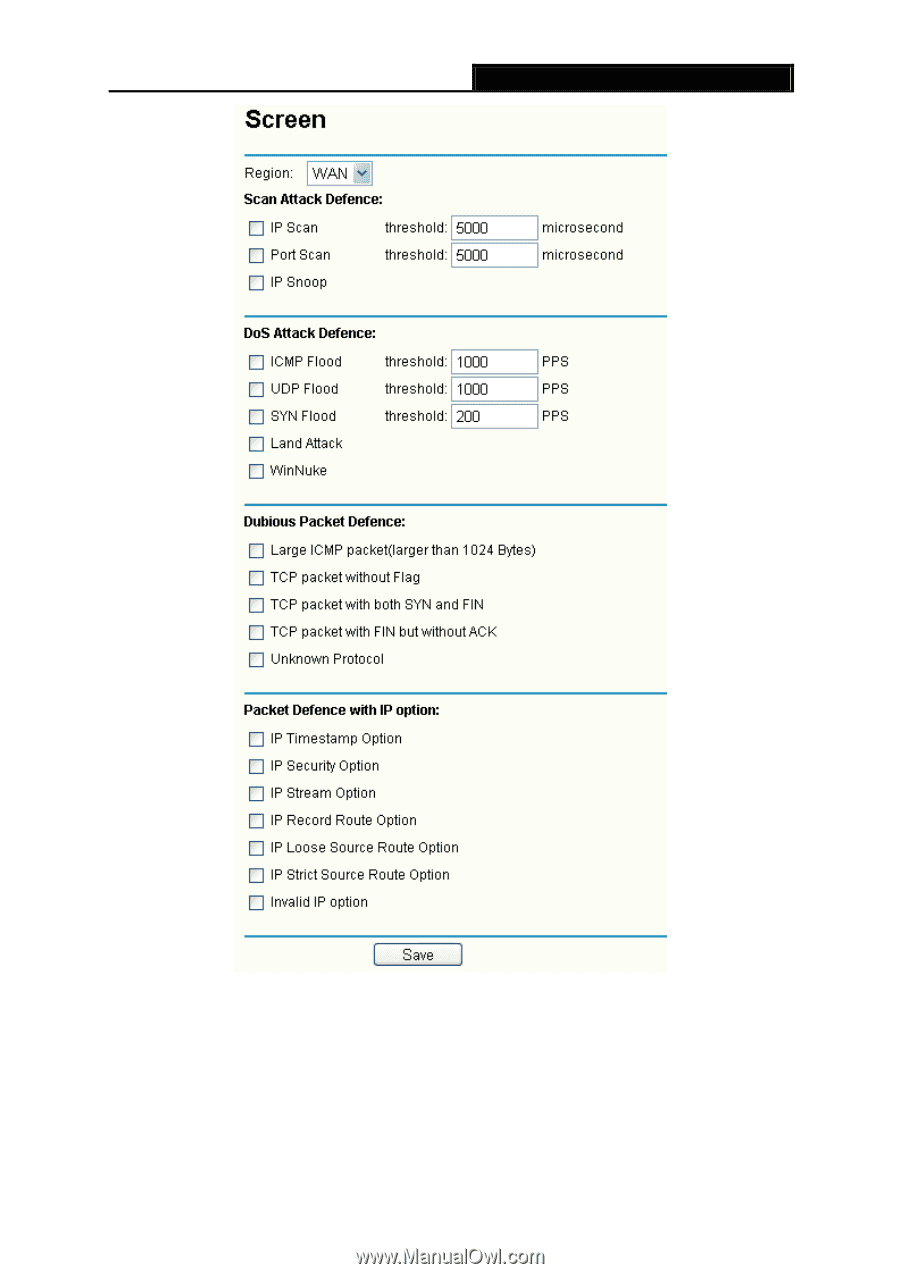
TL-R480T
SMB Broadband Router User Guide
44
Figure 4-37
¾
Region -
This option used to select the specifically area from which the packets will be
monitored by the next settings.
¾
Scan Attack Defence
•
IP Scan:
During the specific time, if a computer (identified by a particular source IP
address) transmits packets to at least ten different computers (identified by different
destination IP addresses), then the source IP address will be deemed to make IP Attacks.
And the Router will start up the blocking function immediately.














