TRENDnet TEW-303PI Manual - Page 39
APPENDIX C: 802.1x Authentication Setup
 |
View all TRENDnet TEW-303PI manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 39 highlights
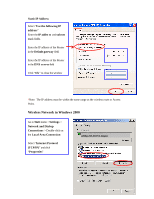
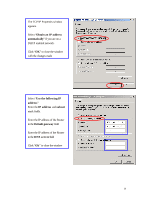
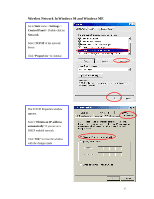
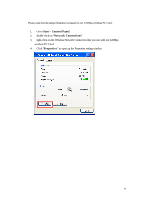
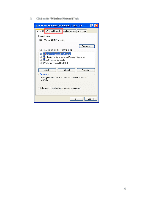
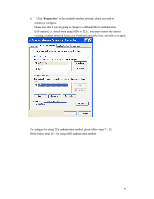
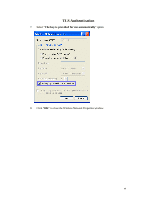
APPENDIX C: 802.1x Authentication Setup There are three essential components to the 802.1x infrastructure: (1) Supplicant, (2) Authenticator and (3) Server. The 802.1x security supports both MD5 and TLS Extensive Authentication Protocol (EAP). The 802.1x Authentication is a complement to the current WEP encryption used in wireless network. The current security weakness of WEP encryption is that there is no key management and no limitation for the duration of key lifetime. 802.1x Authentication offers key management, which includes key per user and key per session, and limits the lifetime of the keys to certain duration. Thus, key decryption by unauthorized attacker becomes extremely difficult, and the wireless network is safely secured. We will introduce the 802.1x Authentication infrastructure as a whole and going into details of the setup for each essential component in 802.1x authentication. 802.1x Authentication Infrastructure 802.11 Wireless Access Points Support 802.1X Authentication Request Public 802.11 Wireless Networks 802.11 Wireless Clients Support 802.1X RADIUS Server Authentication Success Internet/ Intranet The Infrastructure diagram showing above illustrates that a group of 802.11 wireless clients is trying to form a 802.11 wireless network with the Access Point in order to 39