McAfee IIP-M65K-ISAA Product Manual - Page 9
Overview, About IntruShield sensors, Sensor functionality, Network topology considerations
 |
View all McAfee IIP-M65K-ISAA manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 9 highlights
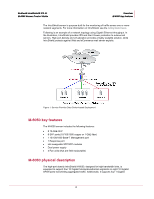
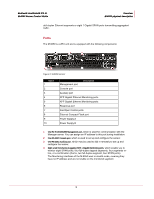
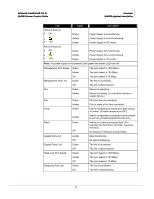
CHAPTER 1 Overview This chapter provides an introduction to IntruShield sensors. About IntruShield sensors IntruShield sensors are high-performance, scalable, and flexible content processing appliances built for the accurate detection and prevention of intrusions, misuse, and distributed denial of service (DDoS) attacks. IntruShield sensors are specifically designed to handle traffic at wire speed, efficiently inspect and detect intrusions with a high degree of accuracy, and flexible enough to adapt to the security needs of any enterprise environment. When deployed at key network access points, an IntruShield sensor provides real-time traffic monitoring to detect malicious activity and respond to the malicious activity as configured by the administrator. Once deployed and once communication is established, sensors are configured and managed using the central IntruShield ISM server. The process of configuring a sensor and establishing communication with the ISM is described in later chapters of this guide. The IntruShield ISM server is described in detail in the Getting Started Guide. Sensor functionality The primary function of an IntruShield sensor is to analyze traffic on selected network segments and to respond when an attack is detected. The sensor examines the header and data portion of every network packet, looking for patterns and behavior in the network traffic that indicate malicious activity. The sensor examines packets according to user-configured policies, or rule sets, which determine what attacks to watch for, and how to respond with countermeasures if an attack is detected. If an attack is detected, a sensor responds according to its configured policy. Sensors can perform many types of attack responses, including generating alerts and packet logs, resetting TCP connections, "scrubbing" malicious packets, and even blocking attack packets entirely before they reach the intended target. Network topology considerations Deployment of an IntruShield IPS requires knowledge of your network to help determine the level of configuration and amount of installed sensors and ISMs required to protect your system. 1