Dell PowerConnect W Clearpass 100 Software ArubaOS Integration Guide - Page 12
ArubaOS Configuration, Creating a RADIUS Server Instance
 |
View all Dell PowerConnect W Clearpass 100 Software manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 12 highlights
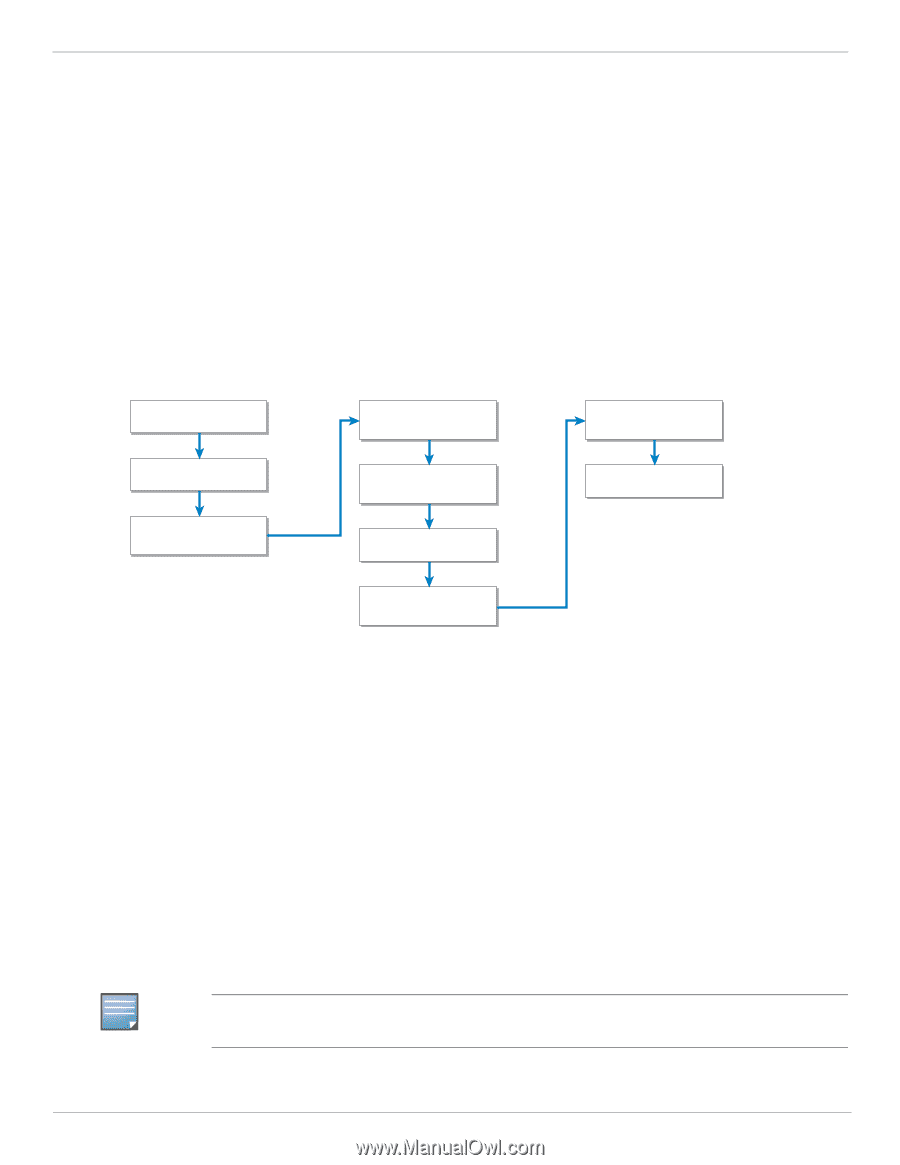
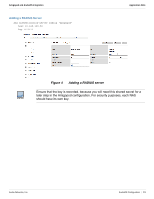
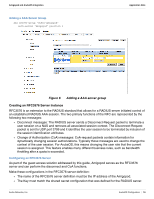
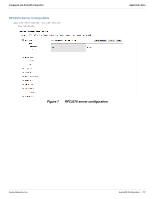
Amigopod and ArubaOS Integration Application Note Chapter 3: ArubaOS Configuration Three phases make up the configuration of the ArubaOS controller to support external captive portal based authentication leveraging the RADIUS protocol: 1. Base RADIUS configuration 2. Captive portal configuration 3. Enabling captive portal on existing guest WLAN Figure 3 summarizes the steps covered in this chapter to successfully complete the ArubaOS configuration that is needed to integrate with the Amigopod external captive portal and RADIUS server. Create RADIUS Server Create Server Group RADIUS Config Create RFC 3576 Server Create Captive Portal Profile Configure Captive Portal Authentication Modify AAA Profile Captive Portal Config Modify initial role for Captive Portal Verify Guest Virtual AP Enable Captive Portal arun_0541 Figure 3 Create PEF policy allow Amigopod Workflow for ArubaOS configuration Creating a RADIUS Server Instance For the Aruba controller to successfully authenticate the guest users that will be provisioned on the Amigopod system, a RADIUS definition must be defined on the controller. The RADIUS server definition requires that the following fields be configured: Host should be configured to the Amigopod IP address. Key is the shared secret that is needed to secure RADIUS communications. Amigopod uses the default ports of 1812 for authentication and 1813 for accounting. The default Retransmit and Timeout value are adequate for most installs The following configuration must be performed on the master controller. This RADIUS definition is then replicated to all local controllers. In a standalone controller deployment, this RADIUS server instance must be created on each controller individually. NOTE Do not set the NAS ID or NAS IP now. You will configure the NAS ID and NAS IP on each controller in the next step. Aruba Networks, Inc. ArubaOS Configuration | 12