Netgear WG511U WG511U User Manual - Page 63
x Port Based Network Access Control, Use WEP for Authentication Only
 |
UPC - 606449037333
View all Netgear WG511U manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 63 highlights
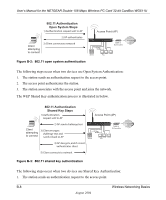
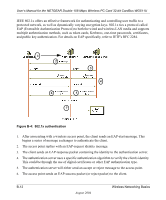
User's Manual for the NETGEAR Double 108 Mbps Wireless PC Card 32-bit CardBus WG511U Note: Some 802.11 access points also support Use WEP for Authentication Only (Shared Key Authentication without data encryption). However, the WG511U does not offer this option. 802.1x Port Based Network Access Control Securing any kind of network involves allowing authorized parties to access traffic and networked resources (e.g., servers, hosts) while blocking outsiders. One essential ingredient in this recipe: permitting or denying physical attachment to the underlying communications medium. In Ethernet LANs, this has long been accomplished by disabling unused RJ-45 jacks and controlling access to Ethernet switch ports according to the Media Access Control (MAC) addresses of the attached device. Early wireless LANs followed suit by using access control lists (ACLs) to permit associations by known MAC addresses while rejecting all others. MAC ACLs are quite easy to understand and configure. However, ACLs become difficult to manage in large dynamic networks and are easily circumvented by network interface cards (NICs) with programmable addresses. The LAN Port Access Control framework defined by the IEEE 802.1X standard addresses these needs. With 802.11 WEP, all wireless access points and client wireless adapters on a particular wireless LAN must use the same encryption key. Each sending station encrypts data with a WEP key before transmission, and the receiving station decrypts it using an identical key. This process reduces the risk of someone passively monitoring the transmission and gaining access to the data transmitted over the wireless connections. However, a major problem with the 802.11 wireless standard is that the keys are cumbersome to change. If you don't update the WEP keys often, an unauthorized person with a sniffing tool can monitor your network for less than a day and decode the encrypted messages. In order to use different keys, you must manually configure each access point and wireless adapter with new keys. Products based on the 802.11 standard alone offer system administrators no effective method to update the keys. This might not be too much of concern with a few users, but the job of renewing keys on larger networks can be a monumental task. As a result, companies either don't use WEP at all or maintain the same keys for weeks, months, and even years. Both cases significantly heighten the wireless LAN's vulnerability to eavesdroppers. Wireless Networking Basics August 2004 B-11