Netgear WG511U WG511U User Manual - Page 68
Wired Network with, WPA 802.1x Port Based, Network Access Control, Wireless Network, Optional
 |
UPC - 606449037333
View all Netgear WG511U manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 68 highlights
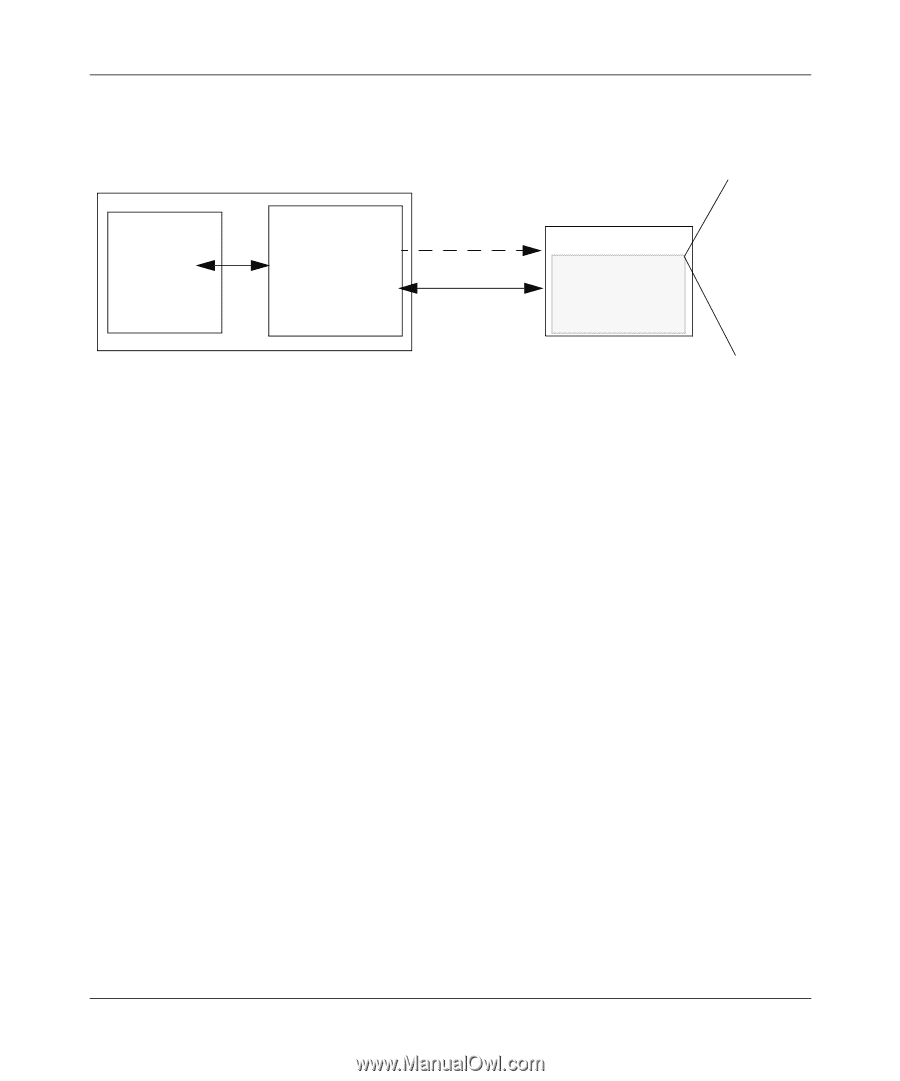
User's Manual for the NETGEAR Double 108 Mbps Wireless PC Card 32-bit CardBus WG511U Wireless Network WPA enabled wireless client with "supplicant" WPA enabled Access Point using pre-shared key or 802.1x/EAP Figure B-5: WPA Overview Wired Network with Optional WPA 802.1x Port Based Network Access Control TCP/IP Ports Closed Until TCP/IP Ports Opened After Authenticated RADIUS Server Login Authentication Optional Certificate Authority (eg Win Server, VeriSign, etc) The strength WPA comes from an integrated sequence of operations that encompass 802.1X/EAP authentication and sophisticated key management and encryption techniques. Its major operations include: • Network security capability determination. This occurs at the 802.11 level and is communicated through WPA information elements in Beacon, Probe Response, and (Re) Association Requests. Information in these elements includes the authentication method (802.1X or Pre-shared key) and the preferred cipher suite (WEP, TKIP, or AES). The primary information conveyed in the Beacon frames is the authentication method and the cipher suite. Possible authentication methods include 802.1X and Pre-shared key. Pre-shared key is an authentication method that uses a statically configured pass phrase on both the stations and the access point. This eliminates the need for an authentication server, which in many home and small office environments will not be available nor desirable. Possible data encryption options include: WEP, TKIP, and AES (Advanced Encryption Standard). We'll talk more TKIP and AES when addressing data privacy below. • Authentication. EAP over 802.1X is used for authentication. Mutual authentication is gained by choosing an EAP type supporting this feature and is required by WPA. 802.1X port access control prevents full access to the network until authentication completes. 802.1X EAPOL-Key packets are used by WPA to distribute per-session keys to those stations successfully authenticated. B-16 August 2004 Wireless Networking Basics