TP-Link T2600G-28MPS T2600G-28MPSUN V1 User Guide - Page 293
ND Detection Process
 |
View all TP-Link T2600G-28MPS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 293 highlights
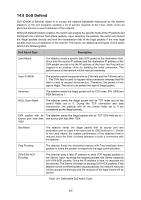
gateway or the other hosts who have received these NS/NA/RS packets will update their ND entry with the wrong address information. AS a result, all packets intended for the victim will be sent to the attacking host rather than the victim host. • The attackers send forged RA packets with the IPv6 address of a victim gateway. All the hosts attached to the victim gateway may receive incorrect IPv6 configuration parameters and maintain false ND entries. A forged ND packet has the following two features: • The source MAC address in the Ethernet frame header is inconsistent with that carried in the source link layer address option of the ND packet. • The mapping between the source IPv6 address and the source MAC address in the Ethernet frame header is invalid. ND Detection Process Generally, the ND detection feature uses the entries in the IPv6-MAC binding table to verify the packets received on the untrusted ports, thus filtering the forged ND packets and keeping out the attacks. 1. ND packets received on the ND-trusted port will not be checked. 2. RS/NS packets with their source IPv6 address unspecified will not be checked. 3. RA/RR packets received on the ND-untrusted port will be discarded directly; the other ND packets received on the ND-untrusted port will be checked. a) Source MAC consistence check. If the RS/NS packet's source MAC address in the Ethernet frame header is different from that carried in the source layer address option, the RS/NS packet will be discarded. b) IPv6-MAC binding check. Look up the IPv6-MAC binding table to compare the IPv6 address, MAC address, VLAN ID and receiving port between the entry and the ND packet. If a match is found, the ND packet is considered legal and forwarded; if no match is found, the ND packet is considered illegal and discarded directly. 282