VMware THIN4-CL-C Deployment Guide - Page 10
Procedural Discussion
 |
View all VMware THIN4-CL-C manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 10 highlights
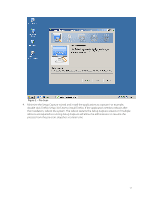
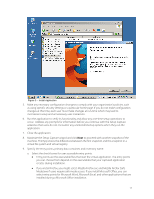
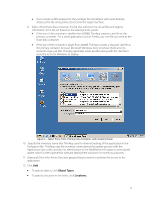
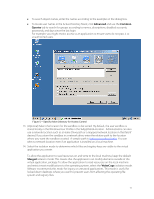
Isolation Mode The term Isolation Mode describes the degree of isolation between the virtualized application and the files, folders, and registry of the local operating system. Administrators use Isolation Mode settings to define which resources of the local operating system are visible to the virtualized application. Isolation Mode settings by default are inherited down through a folder and registry structure. Administrators have granular control to define the appropriate isolation mode settings for each folder and registry sub-tree. The three values for Isolation Modes are Merged, Write-copy, and Full. The following is a link to the online help file which provides further details on Isolation Mode settings: http://www.vmware.com/support/pubs/thinapp_pubs.html Sandbox The sandbox is a user specific folder created for each virtualized application that holds run-time changes to the virtualized registry, folders, and files. The virtualized application maintains the sandbox and utilizes isolation mode settings to determine when to write changes to the sandbox or to the local operating system. The sandbox is located by default in the user's %AppData% location. If folder redirection or roaming profiles are in use then the sandbox simply follows that path. The sandbox folder location is configurable such that it can be located centrally for users to access their application settings from multiple devices. Entry Points Entry points are user accessible starting points for virtualized applications or natively installed applications for use by virtualized applications. Entry points by default correspond to the executables detected during the Setup Capture process and chosen by the administrator to make available to the end user as an entry point into the virtualized application. Procedural Discussion The setup capture process requires the following components as part of a packaging environment that can be used repeatedly for the Capture and Build phase: VMware ThinApp software installed locally or accessible via a network location. For your convenience, VMware makes ThinApp available to customers for a 60-day evaluation period at http://www.vmware.com/go/trythinapp A clean operating system image either physical or virtual with minimal updates and no applications pre-installed. VMware recommends the use of a VM for this function because administrators can take advantage of the snapshot functionality to roll back to the pristine state of the operating system before the application is installed. Purchase or evaluation of VMware ThinApp includes a licensed copy of VMware Workstation for this purpose. Application installation source files and install procedures. Overview of the Setup Capture Process The Setup Capture process begins with a pre-scan of the operating system to provide a baseline for comparison after the application installation. Once the pre-scan is complete, the administrator will install the application, configure the application, and then run the post-scan. The pre- and post- scan make use of operating system level snapshots that record the registry, file and folder structure, and other components affected by the application installation routine. After the postscan the Setup Capture wizard asks the administrator to provide a series of configuration options for entry points, primary data container, inventory name, access control, sandbox location, isolation mode, and compression. 10