Ricoh Aficio MP 6001 SP Security Target - Page 72
Rationale for Removing Dependencies on FCS_CKM.4
 |
View all Ricoh Aficio MP 6001 SP manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 72 highlights
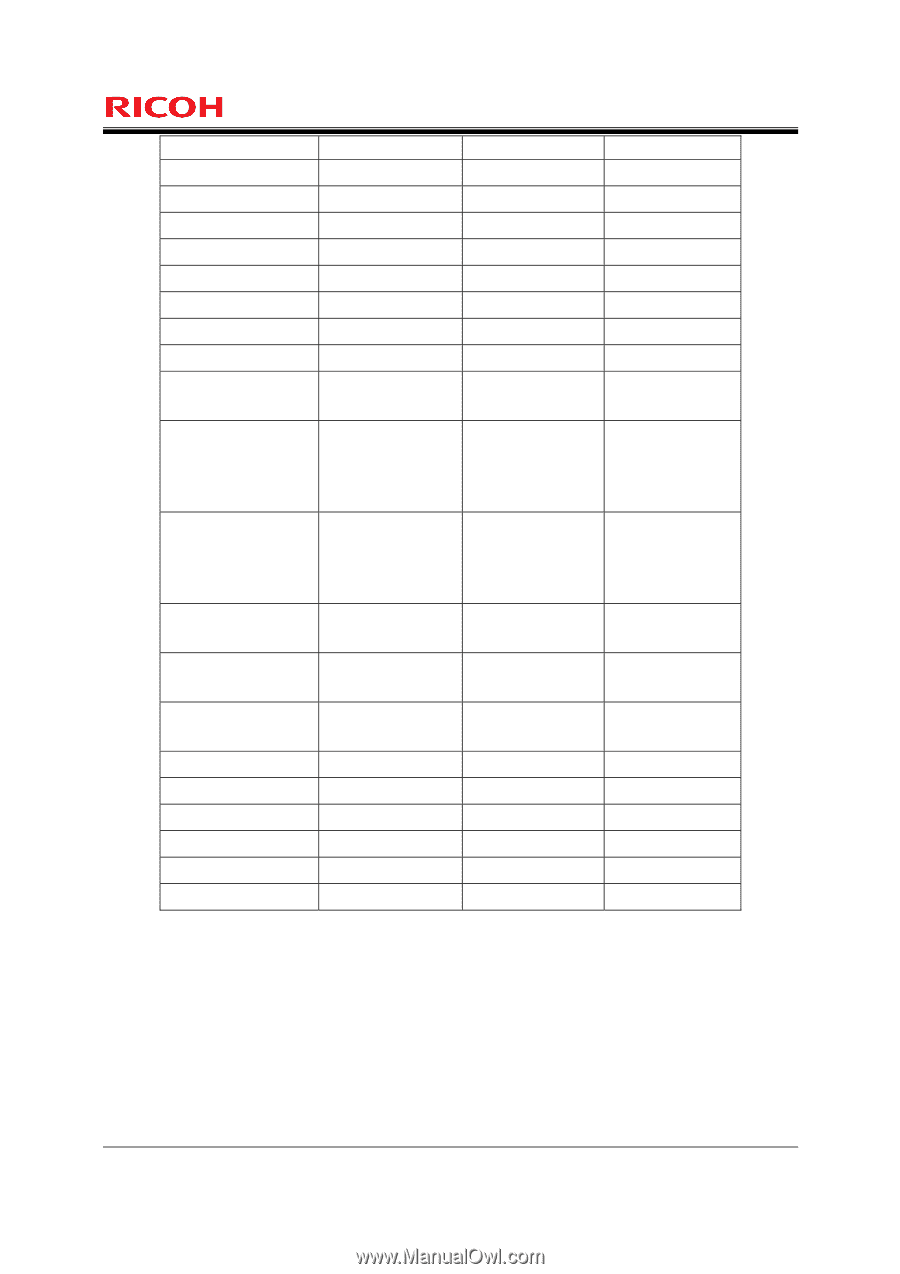
FDP_RIP.1 FIA_AFL.1 FIA_ATD.1 FIA_SOS.1 FIA_UAU.1 FIA_UAU.7 FIA_UID.1 FIA_USB.1 FPT_FDI_EXP.1 FMT_MSA.1(a) FMT_MSA.1(b) FMT_MSA.3(a) FMT_MSA.3(b) FMT_MTD.1 FMT_SMF.1 FMT_SMR.1 FPT_STM.1 FPT_TST.1 FTA_SSL.3 FTP_ITC.1 FMT_MSA.3(b) None FIA_UAU.1 None None FIA_UID.1 FIA_UAU.1 None FIA_ATD.1 FMT_SMF.1 FMT_SMR.1 [FDP_ACC.1(a) or FDP_IFC.1] FMT_SMR.1 FMT_SMF.1 [FDP_ACC.1(b) or FDP_IFC.1] FMT_SMR.1 FMT_SMF.1 FMT_MSA.1(a) FMT_SMR.1 FMT_MSA.1(b) FMT_SMR.1 FMT_SMR.1 FMT_SMF.1 None FIA_UID.1 None None None None FMT_MSA.3(b) None FIA_UAU.1 None None FIA_UID.1 FIA_UAU.1 None FIA_ATD.1 FMT_SMF.1 FMT_SMR.1 FDP_ACC.1(a) FMT_SMR.1 FMT_SMF.1 FDP_ACC.1(b) FMT_SMR.1 FMT_SMF.1 FMT_MSA.1(a) FMT_SMR.1 FMT_MSA.1(b) FMT_SMR.1 FMT_SMR.1 FMT_SMF.1 None FIA_UID.1 None None None None None None None None None None None None None None None None None None None None None None None None Page 71 of 87 The following explains the rationale for acceptability in all cases where a dependency is not satisfied: Rationale for Removing Dependencies on FCS_CKM.4 Once the MFP administrator generates the cryptographic key that is used for the HDD encryption of this TOE at the start of TOE operation, the cryptographic key will be continuously used for the HDD and will not be deleted. Therefore, cryptographic key destruction by the standard method is unnecessary. Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.