TP-Link TL-WN422G User Guide - Page 26
TL-WN422G, Apply, 1.2.3, WPA/WPA2 Authentication with TKIP/AES Encryption, Authentication, - usb wi fi adapter
 |
UPC - 696726422013
View all TP-Link TL-WN422G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 26 highlights
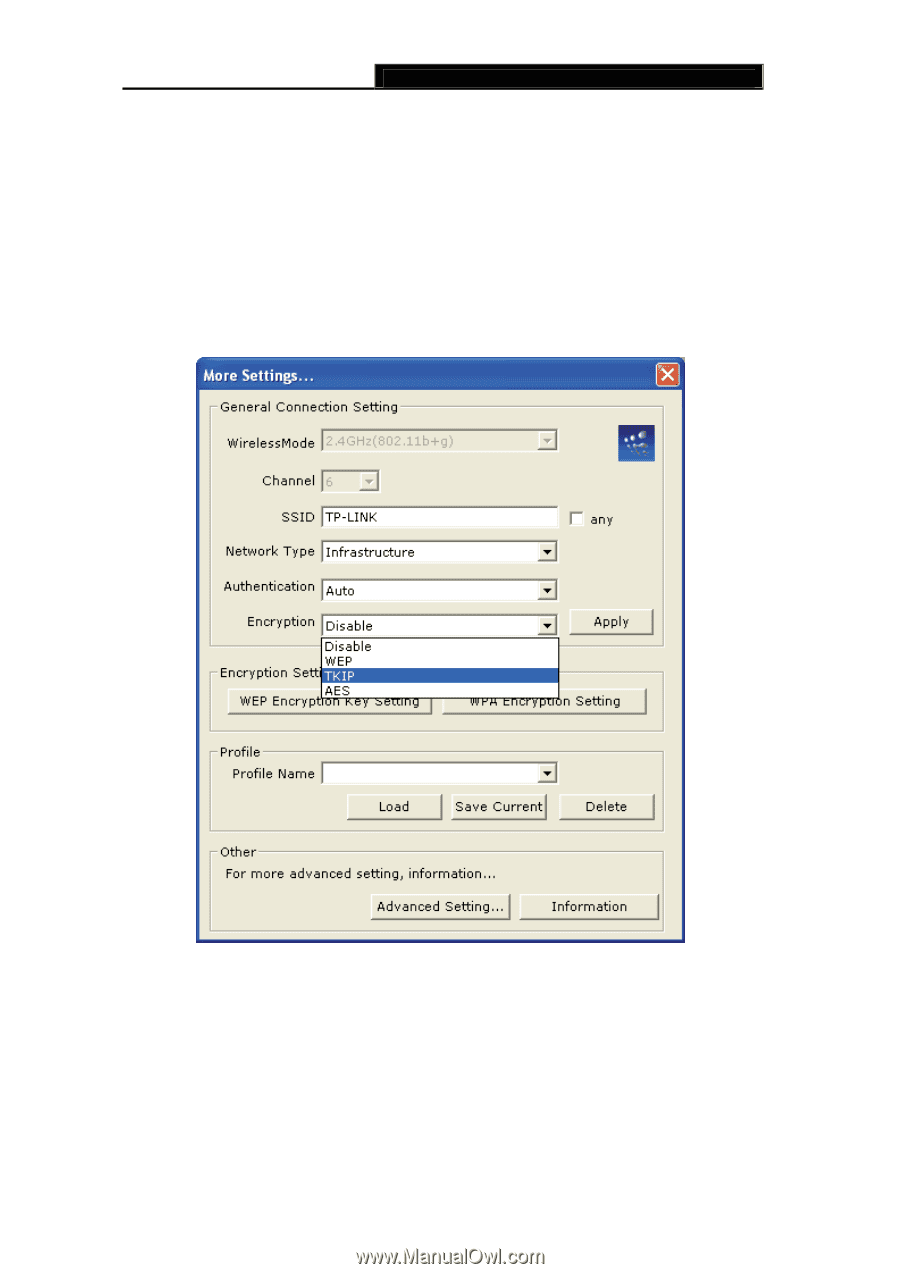
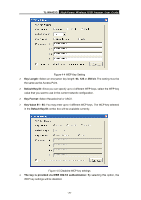
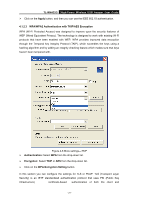
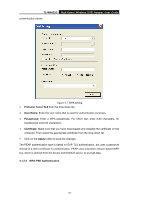
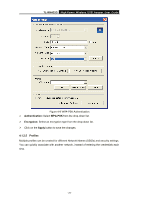
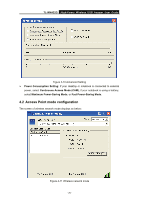
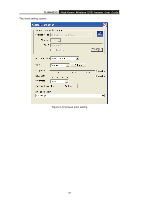
TL-WN422G High-Power Wireless USB Adapter User Guide ¾ Click on the Apply button, and then you can use the IEEE 802.1X authentication. 4.1.2.3 WPA/WPA2 Authentication with TKIP/AES Encryption WPA (Wi-Fi Protected Access) was designed to improve upon the security features of WEP (Wired Equivalent Privacy). The technology is designed to work with existing Wi-Fi products that have been enabled with WEP. WPA provides improved data encryption through the Temporal key Integrity Protocol (TKIP), which scrambles the keys using a hashing algorithm and by adding an integrity checking feature which makes sure that keys haven't been tampered with. Figure 4-6 More settings-TKIP ¾ Authentication: Select WPA from the drop-down list. ¾ Encryption: Select TKIP or AES from the drop-down list. ¾ Click on the WPA Encryption Setting button. In this section you can configure the settings for TLS or PEAP. TLS (Transport Layer Security) is an IETF standardized authentication protocol that uses PKI (Public Key Infrastructure) certificate-based authentication of both the client and - 21 -