HP T5700 HP Sygate Security Agent User Guide - Page 24
Types of Scans, Quick Scans, Stealth Scans, Trojan Scans, TCP Scans - downloads
 |
View all HP T5700 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 24 highlights
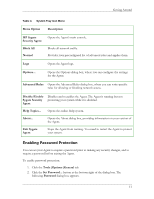
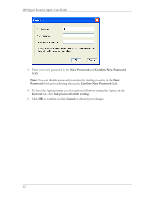
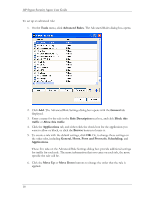
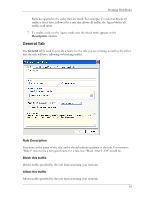
HP Sygate Security Agent User Guide o UDP Scan o ICMP Scan 4. Click Scan Now. A brief document of frequently asked questions about Sygate Online Services is also available from the main scan page. Click Scan FAQ at the bottom left side of the screen. Types of Scans On the Sygate Technologies web site, you can choose from one of the following types of scans. Quick Scans The Quick Scan is a brief, general scan that encompasses several scanning processes. It usually takes 20 seconds or less to accurately scan your device's ports, protocols, services, and possible Trojans. The results are recorded in the Agent's Security Log. Stealth Scans The Stealth scan scans your device using specialized stealthing techniques, which mimic portions of legitimate computer communication to detect the presence of a computer. The Stealth scan takes about 20 seconds to complete and is most likely not recorded in the Security Log. Trojan Scans The Trojan scan feature scans all of your device's 65,535 ports for active Trojan horse programs that you or someone else may have inadvertently downloaded. The Trojan scan takes about 10 minutes to complete. A list of common Trojans is available on the web site. TCP Scans The TCP scan examines the 1,024 ports that are mainly reserved for TCP services, such as instant messaging services, to see if these ports are open to communication. Open ports can indicate a dangerous security hole that can be exploited by malicious hackers. It scans ports on your device that are connected to devices such as routers and proxies for users connecting to the web site through such a device. The scan takes about 20 minutes to complete and is logged by the Agent as a scan event in the Security Log. UDP Scans The UDP scan uses various methods and protocols to probe for open ports utilizing UDP. The UDP scan will scan ports on your device that are connected to devices such as routers 14