HP T5700 HP Sygate Security Agent User Guide - Page 42
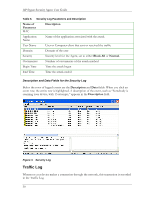
Name of, Parameter, Description, Block All, Normal, Source MAC
 |
View all HP T5700 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 42 highlights
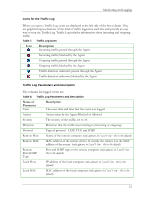
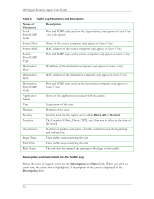
HP Sygate Security Agent User Guide Table 8. Traffic Log Parameters and Description Name of Parameter Local Port/ICMP Code Description Port and ICMP code used on the Agent device (only appears in Local View - this is the default) Source Host Name of the source computer (only appears in Source View) Source MAC MAC address of the source computer (only appears in Source View) Source Port/ICMP Type Port and ICMP type on the source computer (only appears in Source View) Destination Host IP address of the destination computer (only appears in Source View) Destination MAC MAC address of the destination computer (only appears in Source View) Destination Port/ICMP Code Port and ICMP code used on the destination computer (only appears in Source View) Application Name Name of the application associated with the attack User Login name of the user Domain Domain of the user Security Security level for the Agent, set to either Block All or Normal. Location The Location (Office, Home, VPN, etc.) that was in effect at the time of the attack Occurrences Number of packets each piece of traffic sends between the beginning and ending time Begin Time Time traffic starts matching the rule End Time Time traffic stops matching the rule Rule Name The rule that determined the passing or blockage of this traffic Description and Data Fields for the Traffic Log Below the rows of logged events are the Description and Data fields. When you click an event row, the entire row is highlighted. A description of the event is displayed in the Description field. 32