HP T5700 HP Sygate Security Agent User Guide - Page 27
Ch. 4: Working With Rules, About Rules, Using Rules to Protect Your System, Setting Up Advanced Rules - administrator user settings
 |
View all HP T5700 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 27 highlights
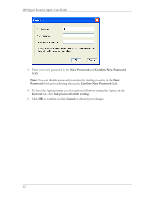
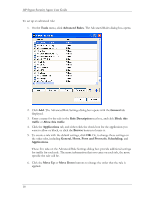
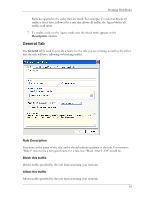
Chapter 4. Working With Rules This chapter describes how to protect your system by creating security rules for applications that you have running on your system. About Rules A firewall is hardware, software, or a combination of both that is used to prevent unauthorized Internet users from accessing a private network. All information entering or leaving the network must pass through the firewall, which examines the information packets and blocks those that do not meet the security criteria. Using Rules to Protect Your System The Agent uses firewall rules, or security rules, to systematically allow or block incoming and outgoing traffic from specific applications, ports, and IP addresses during designated time periods. Each rule specifies the conditions and characteristics (such as the time of day, type of traffic, and port number) that must exist for the rule to take effect as well as the effect the rule has. For example, a security rule may state that "Port 80 is allowed." The Agent supports advanced rules, which exhibit complex relationships between applications, IP addresses, and services. For example, an advanced rule may state that remote port 80 is allowed to devices in subnet 193.58.74.0/24, between 9 AM and 5 PM, Monday through Friday. You can set up your own advanced rules or import them from an administrator or third party. Setting Up Advanced Rules When you set up an advanced security rule, first decide what effect you want the rule to have. For example, do you want to block all traffic when your screensaver is on? Would you like to allow all traffic from a particular source? Do you want to block UDP packets from a web site? 17