HP T5700 HP Sygate Security Agent User Guide - Page 38
Viewing Logs, Security Log, Tools|Logs, Traffic Log, Packet Log, System Log, Local View, Source View
 |
View all HP T5700 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 38 highlights
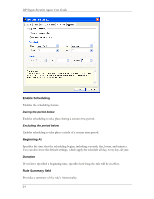
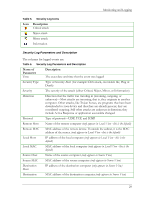
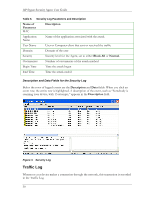
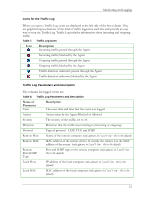
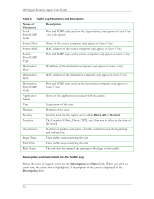
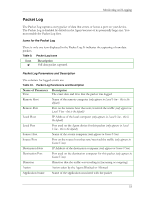
HP Sygate Security Agent User Guide Viewing Logs To view logs on the Agent: 1. Do one of the following: o Click Tools|Logs. o On the toolbar, click the drop-down arrow next to the Logs icon. Note: Click the Logs icon to display the most recently viewed log. 2. Click one of the following log types: Security Log, Traffic Log, Packet Log, or System Log. Each log opens the Log Viewer dialog box. The Log Viewer is a data sheet, where each row represents a logged event, and the columns display information regarding the event. For more information on the differences between the icons and parameters of each log, see Security Log, Traffic Log, Packet Log, and System Log. 3. In the Log Viewer dialog box, click the View menu and click either Local View, the default setting, or Source View. Depending on whether you choose the local view or source view, you can view various options, which vary between each log. 4. In the View menu, click a different log name if you wish. 5. Click Refresh or press F5 to update the log that you are viewing. 6. Click File|Exit to close the log. Security Log The Security Log records potentially threatening activity directed towards your device, such as port scanning, or denial of service attacks. The Security Log is probably the most important log file in the Agent. Icons for the Security Log When you open a Security Log, icons are displayed at the left side of the first column. These are graphical representations of the kind of attack logged on each line, and they provide an easy way to scan the Security Log for possible system errors. 28